Published: Jan 17, 2025
Securing 5G: Evaluating and enhancing network security
introduction
5G networks promise to bring significant improvements over 4G including faster data rates, ultra-low latency, and massive device connectivity. They also support new capabilities such as network slicing and edge computing to enable multiple 5G services. These 5G networks are designed with improved security features based on cybersecurity principles such as ‘defence-in-depth’, ‘zero trust architecture’, and ‘secure by design’. However, the complexity that comes with 5G networks inadvertently increases the attack surface and adds security risks for 5G network operators and users. The key challenge that enterprises face today is how to implement the security required to protect their 5G services against cyber threats without impacting the operational benefits of the 5G network.
To address this challenge, NCS worked with the Cyber Security Agency of Singapore (CSA), a part of the Prime Minister’s Office that is managed by the Ministry of Communications and Information, to conduct a comprehensive study on how available cybersecurity solutions could impact the effectiveness and performance of the User Equipment (UE) deployed within 5G networks. As 5G technology is still relatively new, there are no established guidelines to study the performance impact of the cybersecurity solutions on the UE in 5G networks. NCS developed the following evaluation framework to address this need:
- Identify suitable 5G use cases that include a range of 5G applications
- Define the security features by level of security
- Collect and process data for analysis
- Assess the operational impact of different configurations of security features on the UE in the 5G network
- Conduct a gap analysis to identify and address 5G cybersecurity gaps to further advance 5G cybersecurity solutions in the industry
Identification of 5G use cases
The use cases for the NCS study were selected after consultation with stakeholders to identify cases that cover a range of 5G applications and performance metrics. These use cases are as follows:
- Teleoperations over 5G to simulate the robotics and teleoperation industries
- Video streaming and facial recognition over 5G to simulate 5G video analytics operations applied across multiple industries
- Mixed reality over 5G to simulate 5G applications of mixed reality devices in operational environments (i.e., usage in healthcare settings)
- 5G Network slicing to test the availability and reliability of slicing capabilities of the 5G network
The diagram below shows how the use cases were set up in the 5G testbed and Multi-access Edge Computing (MEC) over a 5G network.
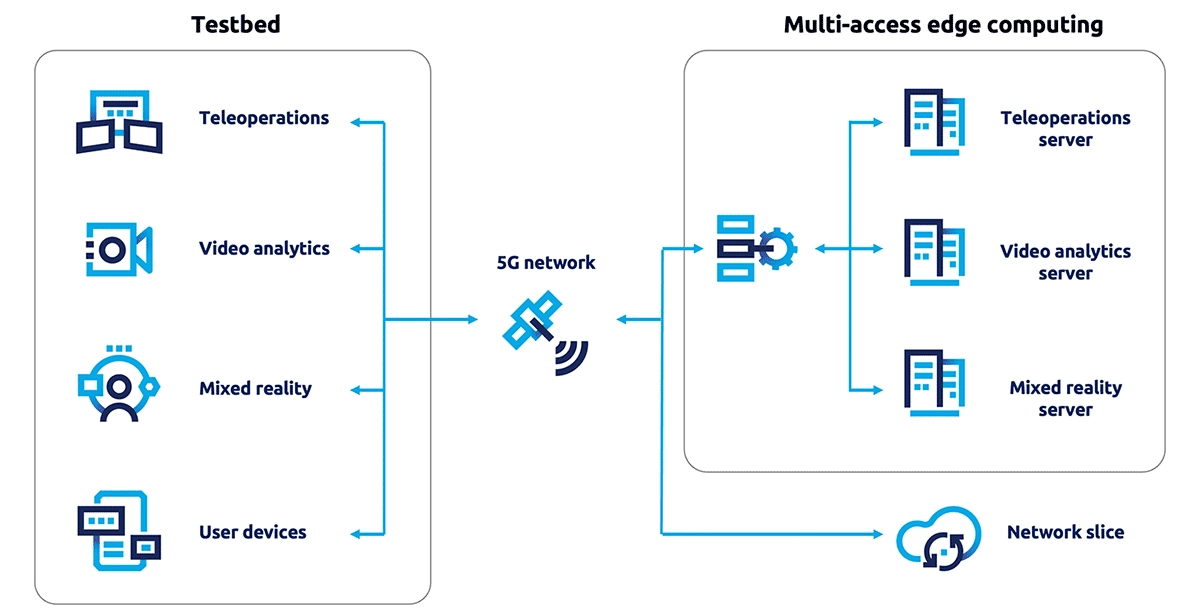
Figure 1: An overview of our 5G testbed setup
The performance metrics selected for the study were throughput, latency, battery consumption, CPU usage, and memory usage. Metric selection was based on the ability to assess impact on operations (i.e., an increase in latency and battery consumption may impact performance of a teleoperations application over 5G).
For testing purposes, all UE deployed in the use cases should ideally be 5G-native to ensure end-to-end secure communication over the 5G network. If the UE deployed cannot be 5G-native (due to device limitations), it should be securely connected, either wired or wirelessly, to 5G Customer Premise Equipment (CPE) or other 5G devices to ensure secure end-to-end connectivity to the 5G network.
Definition of security features
To assess the impact on operations, at each security level, across use cases, the required security features at each level must first be defined so that they can be implemented on the UE. The hypothesis is that the performance impact is related to the number of security features and the security settings used. By way of illustration, a UE should be expected to have high CPU usage if a large number of security features, with high security settings, is used.
As there is no generally agreed framework for defining these security features at different security levels, established 5G cybersecurity standards such as those provided by the U.S. National Institute of Standards (NIST) and the European Union Agency for Cybersecurity (ENISA) were used as the basis for selecting the relevant security features and mapping those features across different security levels. For instance, there is no agreement on the security features required for a ‘baseline security’ level, while a ‘low security’ level must have the minimum number of security features and lowest security settings (e.g., AES-128) required to secure the UE in the 5G network. A ‘high security’ level will have all security features enabled and set to the highest security settings (e.g., AES-256) on the UE.
All security features should be available within the identified cybersecurity solution to ensure an end-to-end performance evaluation, however, as a practical matter, there is no cybersecurity solution that can fully cover all security features. For instance, some security features may not be available due to factors such as an unsupported device operating system or a lack of market demand for the security feature. As such, there is a need to identify and address these cybersecurity gaps through a gap analysis.
Data collection and process
The data collected for assessing performance metrics should be automated, to the extent possible, using data logging to minimise human error and workloads. Automation can be achieved through installing agents within the UE or via simple written codes that log data during measurement and retrieve the data after the measurement is completed. Data formats should be standardised to support data processing and analysis. Measurement should be performed as close to the application layer as possible, and live traffic from the application should be used for measurement to ensure the most accurate representation of the user experience during operation.
Multiple runs should be conducted to collect as much data as possible to derive the average, upper limit, and lower limit of the performance metric. The average can be used to determine the typical value of the performance metric, and the upper and lower limits will determine the spread of the performance metric.
Operation assessment
After data is collected and processed for the performance metrics measured in each of the use cases based on different security levels, the results of the performance metrics at low to high security levels can be compared against the baseline security level to determine the percentage change in the performance metrics. For instance, a 50% increase in latency translates to a two-fold increase in response time, and a 50% increase in battery consumption means that the battery-operated device can last only half as long. This will provide a comprehensive and quantitative assessment of the operational impact for each use case.
Gap analysis
After the assessment of impact to operations is completed, a gap analysis should be conducted to compare the available security features used during the study versus the required security features. This will help to identify the gaps in the security features for 5G devices and point to recommendations, such as development of security features, to bridge the gaps. The key findings from the gap analysis performed by NCS in its study are as follows:
- Not all security requirements for 5G devices can be covered by a single security solution. A combination of solutions is required to secure the 5G devices and network. Devices should be carefully selected to ensure that they can support the security features provided by vendors.
- Vendors can develop new security features to address the identified feature gaps in their product roadmaps. However, development will be dependent on several factors such as market trends and user demand for the security features in 5G devices.
- Some security features can be developed in-house through writing software code to build customised applications.
- System integration is required to ensure different security solutions can interoperate within the same 5G devices and network with minimal performance impact or impact to operations.
NCS strategy for 5G security
NCS possesses the necessary skills, resources, and capabilities to address the 5G cybersecurity gaps and further advance 5G cybersecurity solutions in the industry. These include:
- A suite of 5G professional services that is built on the expertise of NCS and its partners in areas such as compliance and risk management
- A team of qualified and certified cyber professionals with unique domain knowledge in IT, OT/ IoT, and 5G security
- Strong research capabilities and close collaboration with the National University of Singapore (NUS) and leading cybersecurity vendors
Conclusion
5G capabilities such as network slicing are still evolving. There is a need to stay current on the latest 5G cybersecurity technical solutions that will protect critical 5G systems and services against emerging threats. At the same time, there is also a need for a balance between meeting cybersecurity needs and ensuring minimal impact to the performance of 5G services.
This evaluation framework provides a systematic approach to validating the most suitable security configurations that will maximise 5G benefits and minimise impact to operations, based on use case. At the same time, it also allows enterprises to identify 5G cybersecurity gaps, so that system integrators, such as NCS, can develop the required security features to meet the enterprise’s operational and security requirements.
References
Cybersecurity Agency of Singapore. (2022). Guidelines for CII Owners to Enhance Cyber Security for 5G Use Cases.