Published: Jan 17, 2025
Navigating quantum-safe development and its imperatives
Executive summary
In today's rapidly evolving digital landscape, the emergence of quantum computing presents both a challenge and an opportunity. Businesses that fail to prepare for quantum-safe security may face significant risks, including data breaches and a loss of competitive advantage. This summary highlights the essential steps and benefits of transitioning to quantum-safe practices to ensure that your business remains secure, competitive, and future-proof.
Our world depends on digital infrastructure and digital communications – all of which inherently rely on cryptography to ensure trust. Cryptographic technologies are used throughout governments and enterprises across a variety of industries, to authenticate sources and protect the confidentiality and integrity of the information that we communicate and store. Cryptographic technologies include a broad range of protocols, schemes, and infrastructures.
Trust is at risk as asymmetric cryptography is likely to be broken when a Cryptographically Relevant Quantum Computer (CRQC) becomes available. This risk extends to symmetric cryptography, which will not be directly impacted, but will require new strategies for mitigation as well. As quantum computing advances, organisations face the need to protect their sensitive data from potential vulnerabilities.
The quantum computing era will unfold over time, but the need for quantum-safe solutions is immediate. The strategic planning, preparation, and remediation effort required to support crypto systems, even pre-quantum computing, can require several years because of the complexity involved. Business, technology, and security leaders face an urgent need to develop quantum-safe strategies and quantum-computing roadmaps now.
The IT landscape has become increasingly complex over the years. This landscape is composed of many components including internally developed digital applications, IT capabilities inherited through acquisitions, third party software products and SaaS, and services consumed from cloud providers. The scope of technology that organisations need to upgrade to become quantum-safe, or remediated to use quantum-safe cryptography, is significant. As a result, it is not unreasonable to anticipate several years of effort for an enterprise to become quantum-safe.
Developing quantum-safe cryptography capabilities is crucial to maintaining data security and integrity for critical applications. This includes developing and applying cryptographic agility approaches to switch between multiple cryptographic primitives without making any major changes to infrastructure to ensure a rapid response to any cryptographic threat.
Cryptographic agility requires more than just an inventory of cryptographic assets and usage. It requires having the relevant information, at the right time, in the right place, with the right governance. A programmatic and iterative quantum-safe programme, developed in collaboration with stakeholders, will provide a structured approach to implementing quantum-safe solutions that adapt to emerging threats and continuously improve overall security.
Planning for quantum-safe
The scope of what needs to be upgraded to be quantum-safe or remediated to use post-quantum cryptography (PQC), is significant. The journey to a quantum-safe future must be well planned and incrementally executed based on business and technical priorities and several other critical considerations. The following provides an overview of critical steps to consider on the journey to a quantum-safe future:
-
Inventory current cryptography usage:
The first step is to ensure a comprehensive understanding of cryptography usage across the organisation. This can be achieved by developing an inventory of both the static and dynamic view of cryptography usage. The scanning of cryptography usage in custom applications used within an organisation provides a static view, and scanning networks for cryptography calls provides a dynamic view of cryptography usage. This comprehensive inventory of cryptography usage is best represented in a standard form such as a Cryptography Bill of Materials (CBOM). -
Identify and prioritise ‘crown jewels’:
Having a comprehensive inventory is necessary but not especially useful from a planning perspective. It is critical that the ‘crown jewels’ (i.e., the most critical data and assets with your organisation) are identified and safeguarded first. This can be achieved by classifying all assets within the organisation, based on both business and technical importance, and weighing the criticality of each asset. The resulting prioritised view of the asset landscape can then be used to develop a transformation plan or roadmap. - Develop a transformation roadmap:
It is not possible to transform all applications and systems in one massive initiative. The transformation must be broken into several phases, with each phase building on the collective experiences and capabilities of prior phases. Developing such an incremental transformation roadmap is a particularly important step and must be undertaken with great thought and a depth of understanding of the challenges involved. This is typically a transformation where the implementation team starts small, learns from each iteration, builds reusable components, establishes comprehensive transformation approaches, and executes these diligently over several years. The scope of the transformation must include systems within the control of the organisation, and outside of the organisation. External or third-party entities that integrate with the organisation’s systems must also complete their own transformations.
- Begin transformation to become quantum-safe:
Having developed an actionable transformation roadmap, beginning to execute against that plan is the next step. The transformation journey will typically take several years. Given this expected project duration, it is important that the transformation roadmap be periodically validated with findings from the ongoing transformation, as well as other environmental considerations and changes, and adjusted accordingly. One key aspect of this transformation step is ensuring that ‘crypto agility’ is part of the transformation. Ensuring that future cryptography-related changes do not require core changes to an application is what is typically referred to as crypto agility. This assurance allows for ease of transition from one post-quantum cryptography algorithm to another in the future, should the need arise. All activities must include enabling crypto agility as part of the transformation.
Another key aspect of the transformation step is to not assume that the effort is simply one where old cryptography technology is replaced with new post-quantum cryptography. While this is indeed one approach, it is not the most efficient or effective way. Identifying the appropriate remediation approach or pattern for transforming an application or system is important. It is very likely that organisations with a lot of applications can establish and use multiple patterns repeatedly across their IT landscapes.
- Gain familiarity and expertise in the use of new algorithms:
An activity that must be undertaken right from the start, and executed in parallel with the previously enumerated steps, is to establish a credible level of competency in the judicious application of post-quantum cryptography. The new post-quantum cryptography algorithms are quite complex and are quite different from existing algorithms. Understanding the appropriate use of the algorithms, and their performance profiles and resource consumption characteristics, among other factors, is very important.
This level of competency can be achieved by establishing a centre of excellence, and by identifying dedicated cryptographic engineers and security architects and providing them with an environment and opportunities to experiment and learn. For learning purposes, establishing a sandbox to test new algorithms in the organisation’s environment is very important, as is the execution of targeted pilot projects.
Recent developments in quantum computing
The world is on the cusp of another computer revolution that will be driven by the convergence of powerful technologies, chief among which are high-performance computing, Artificial Intelligence (AI), and quantum computing. Quantum computing is not simply a faster way of doing what today’s computers do – it is a fundamentally different approach that promises to solve problems that classical computing can never realistically solve. It holds the promise to help humanity confront important challenges, from solving long-standing questions in science, to overcoming obstacles in improving industrial efficiency. Working in conjunction with classical computers and cloud-based architectures, quantum computers could even be the answer to problems we haven’t yet dreamed of. The benefits to society and the economic opportunities are potentially limitless.
In the case of quantum computing, the theme of the past few decades has been the emergence and establishment of this innovative technology. The quantum community has been focused on laying the groundwork: experimenting with quantum hardware, devising use cases, and educating people on how to use quantum computers, while running experiments benchmarking devices. Recently, IBM made quantum computing real.
A June 2023 paper by IBM and UC Berkeley outlines a path toward useful quantum computing.Read here for new insights into how we demonstrated that quantum computers could run circuits beyond the reach of brute-force classical simulations. For the first time, IBM has hardware and software capable of executing quantum circuits with no known a priori answer at a scale of 100 qubits and 3,000 gates. Quantum is now a computational tool, and what makes us most excited is that we can start to advance science in fields beyond quantum computing itself. It is clear that a heterogeneous computing architecture consisting of scalable and parallel circuit execution and advanced classical computation is required. This has culminated in IBM’s vision for high-performance systems for the future: quantum-centric supercomputing (IBM Debuts Next-Generation Quantum Processor & IBM Quantum System Two, Extends Roadmap to Advance Era of Quantum Utility).
The quantum threat
The security of most standard algorithms relies on extremely difficult mathematical problems that take years to solve with current computers. Modern public-key encryption protocols are satisfactory for protecting against most of the technological tools at the disposal of today’s threat actors. However, that won’t last. Quantum computers will be capable of breaking these math-based systems in a matter of seconds. In addition, threat actors are now harvesting large quantities of encrypted data and storing it until they can break the encryption keys using quantum computing. Data that is encrypted today is vulnerable to decryption tomorrow.

Quantum Readiness Toolkit: Building a Quantum-secure Economy, World Economic Forum, 20231
When large-scale quantum computers are built, they will be capable of breaking many of the current public-key cryptography systems. Global funding for quantum computing start-ups increased by 13.5% last year, to $1.1 billion. According to McKinsey, China plans to invest $15.3 billion in the industry, and the European Union has set aside $7.2 billion for investment. Without significant preparation for moving to post-quantum cryptography, quantum computers in the wrong hands could significantly compromise the privacy and security of the digital communications that the world increasingly relies on.
Why start preparing now?
The question of when cryptography will be broken by quantum computing is unfortunate as it implicitly frames the threat as some time in the future, when in reality, the threat exists today, but the impact will only be felt in the future. Data that is considered securely protected today has already been lost to a future quantum adversary if it has been stolen or harvested. All data, past, present, and future, that is not protected using quantum-safe security, is at risk, and the longer we postpone the migration to quantum-safe standards, the more data there will be that is at risk.
Our experience makes it clear that there will not be a one-size-fits-all strategy when it comes to migrating to quantum-safe security. Given the long-term nature of the threat, and the dynamic environment surrounding quantum computing, it is also clear that a cryptographic strategy needs to consider multiple time frames address potential step improvements in quantum technology development. Governments have a role to play. To supplement the private sector’s engagement in standards development, governments need to accelerate investment in, and promote the adoption of, quantum-safe cryptographic solutions that can safeguard data now and long into the future.
The threat of Cryptographically Relevant Quantum Computers (CRQC) is significant, but the timeline for when that threat will be realised is unknown. How can an organisation quantify the risk of CRQCs when they don’t yet exist? The immediate best practice suggests creating several scenarios of the risk of a quantum threat to a specific asset, with some of these scenarios deemed as “more likely” than others.
The argument for starting to address the threat that quantum computers will pose to existing security systems now, is based on the following considerations:
-
Cryptographic technologies are integrated into most of the digital products commonly used by organisations to run their daily operations.
-
Some of the applications and systems used in the infrastructure within the energy, transportation, finance, and government sectors have product lifetimes of 15 to 30 years, and requirements for data protection and privacy are even longer.
-
The time needed to migrate installed cryptographic technologies (e.g., SHA1) to something newer is usually measured in years.
-
The cryptographic systems that organisations will need to migrate to new “quantum-safe” cryptography will be numerous.
-
Most organisations have no clear view of the cryptographic technologies used in IT operations and this will make it difficult to discover, and then prioritise, the systems to be upgraded to post-quantum cryptography.
Guiding principles for preparing a quantum-safe journey
The World Economic Forum (WEF) recently published a set of guiding principles that outline the steps that organisations can take to become quantum cyber-ready [WEF23] in preparation for a quantum-secure economy. The guidelines also highlight the importance of a cohesive global and cross-border approach to governing quantum that includes involving business stakeholders and experts from business, governments, regulators, and academic institutions. However, as organisations vary in size, industry, and maturity, there is no single approach or strategy that serves as a one-size-fits-all solution.
We outline five key guiding principles that any organisation should consider as it starts to prepare for the transition to quantum-safe security.
Look beyond the development time frame for quantum computing
In contemplating the potential impact of quantum computing on the digital landscape, it is crucial to adopt a forward-thinking perspective that extends beyond the technology’s current developmental stage. Quantum computing holds transformative potential, yet remains an active area of research, with scientists exploring more reliable and scalable methods. Attempting to predict precisely when quantum computers will break existing encryption technology is challenging, so strategic preparation efforts should be decoupled from specific development timelines. Relying solely on projected quantum computing evolution can create a false sense of security. Instead, organisations should focus on building a robust cybersecurity foundation, with quantum-resistant algorithms, irrespective of the uncertain future arrival of quantum computers. This approach involves developing cryptographic strategies that are not time-dependent, embrace post-quantum cryptography (PQC), and continuously enhance security. By building in adaptability and resilience, organisations can proactively secure digital assets in preparation for the full realisation of quantum computing.
Understand where you are now
Preparing for the imminent era of quantum computing requires organisations to proactively strengthen their cybersecurity defences. A foundational step in this process is conducting a thorough cryptography inventory and assessment, and this is especially crucial for entities that safeguard data requiring prolonged protection. The scrutinisation of cryptographic infrastructure allows organisations to identify vulnerabilities and bolster defences against quantum computing threats. This preparatory phase involves the identification of assets and systems that rely on cryptography, and emphasis should be placed on those using vulnerable algorithms such as RSA and ECC. Prioritisation is critical. Organisations should categorise systems based on data criticality to strategically allocate resources. Evaluating the potential impact of transitioning to quantum-resistant algorithms ensures a seamless integration without compromising operational efficiency. This proactive approach positions organisations to navigate the challenges posed by quantum computing effectively.
Establish a governance framework
Establishing quantum-safe security requires a meticulous approach and the active involvement of senior executives in the establishment and enforcement of a robust governance structure. A dedicated governance team should oversee the entire process to ensure alignment with organisational goals. This involves developing a quantum-safe roadmap which is in sync with quantum risk assessments and the organisation’s risk appetite.
Moreover, integrating quantum risk into the existing cybersecurity operating model fortifies defences against emerging threats. Designating cryptographic ‘champions’ within the organisation will help to socialise the potential impact of quantum risk and drive the implementation of quantum security plans. In essence, effective governance will form the foundation for successful quantum security projects by instituting robust structures and mandates that ensure clear direction and accountability throughout the quantum-safe transition.
Hybrid approach
In enhancing cybersecurity against the uncertainties introduced by quantum computing, a prudent and conservative approach is essential. We advocate a strategy embracing a hybrid approach that strategically combines classical and quantum-safe cryptographic algorithms. A nuanced strategy will include the consideration that today’s quantum-safe algorithms may encounter future challenges from computing advancements or unforeseen weaknesses, as has often been the case throughout the history of cryptography. By adopting a multi-layered defence mechanism through a hybrid approach and not relying solely on the resilience of a single cryptographic algorithm, organisations can more efficiently fortify their security postures. This approach may involve combining classical and quantum-safe algorithms, or the integration of multiple quantum-safe algorithms that have distinct properties. A forward-looking strategy should emphasise adaptability and robustness and reflect a commitment to proactive security measures that are diverse and redundant.
Continuous capability development
In the pursuit of quantum-safe security, continuous capability development is crucial for organisations seeking a proactive and adaptive transition. This involves conducting small-scale pilots to validate PQC solutions in real-world scenarios to assess performance, compatibility, and integration challenges. These pilots will yield valuable data and feedback that will inform and enhance the overall migration strategy. Simultaneously, employee education should play a leading role in raising awareness about quantum computing risks, and the necessity for migration. Training programmes will empower workforces with knowledge and the skills to securely use and manage quantum-safe systems, while helping to establish a culture of cybersecurity awareness. Continuous monitoring of PQC implementations will ensure the ongoing identification of vulnerabilities and performance issues that will be crucial for staying ahead of the evolving quantum threat landscape. The governance team should remain agile and adapt security measures based on emerging challenges and insights gained through ongoing monitoring. Regular tracking of standardisation efforts by organisations like NIST and ETSI will solidify the organisation’s commitment to quantum-safe security and ensure alignment with industry best practices and standards. Through these multifaceted efforts, organisations can fortify their capabilities and readiness to navigate the quantum era with resilience and foresight.
Adopting quantum-safe practices isn't just about security; it's a strategic business move. In this subsection, we translate technical principles into business strategies and detail how being ‘quantum-safe’ can be a unique selling point and enhance customer trust.
Risk management
Strategy and preparation
Our experience shows that the journey to ‘quantum-safe’ must be well planned and incrementally executed based on a number of considerations including business and technical priorities. An effective quantum-safe approach combines technology with first-step guidance to prioritise quantum-safe initiatives, and to assess organisational risk, IT strategy, supply-chain dependencies, and ecosystem operations. Core to this approach is the creation of cryptographic inventories as well as corresponding risk and governance plans. Quantum-safe migration is a multi-step process requiring both operations and cryptographic experience. Alignment with broader business transformation efforts is another dimension for effective planning across this multi-year initiative. External factors involving regulatory agencies, standards bodies, and ecosystem partners must also be considered.
IBM Quantum Safe approach
The IBM Quantum Safe approach combines first-step guidance for prioritisation with IBM Quantum Safe technology that is tailored to meet clients’ organisational risk, IT strategy, supply-chain dependency, and ecosystem operational objectives. The IBM Quantum Safe offering extends to include capabilities designed to provide a better understanding of applications and network operations. The overall approach supports a quantum-safe change programme through the creation of cryptographic inventories and corresponding risk and governance plans.
There are two main elements:
Strategy: Services designed to enable clients to initiate a quantum-safe transformation programme and prepare to fund and scale the programme across the organisation. The IBM Quantum Safe programme establishes an approach to assess the requirements to transition to quantum-safe cryptography and creates a plan for adoption. The approach includes clear phases and outcomes via agile information collection methods with delivery dependencies and parallel activities.
Technology: Designed to guide clients through initial pilots to demonstrate the ability to accelerate the transition to quantum-safe cryptography, accelerate the remediation of applications within the enterprise, and establish a programme for full-scale deployment.
IBM Quantum Safe technology offers a comprehensive set of capabilities and approaches, combined with deep expertise, to help plan and execute a migration to quantum-safe cryptography. Quantum cyber resilience can be carried out over three phases—Discover, Observe, and Transform—each powered by IBM Quantum Safe technology:
-
IBM Quantum Safe Explorer can enable organisations to scan source and object code to locate cryptographic assets, dependencies, and vulnerabilities to build a CBOM. This allows teams to view and aggregate potential risks into one central location.
-
IBM Quantum Safe Advisor enables the creation of a dynamic or operational view of cryptographic inventory to guide remediation and analyses cryptographic posture and compliance to prioritise risks. Quantum Safe Advisor performs an enterprise-wide analysis of your cryptography and builds a comprehensive cryptographic inventory that details the types and locations of your cryptographic instances, the relationships between assets and data flows, and potential vulnerabilities to quantum technology.
-
IBM Quantum Safe Remediator enables organisations to deploy and test best-practice-based quantum-safe remediation patterns to understand the potential impact on systems and assets as they prepare to deploy quantum-safe solutions. Remediator helps organisations to create an architecture for seamlessly upgrading cryptographic infrastructure to become quantum-safe.
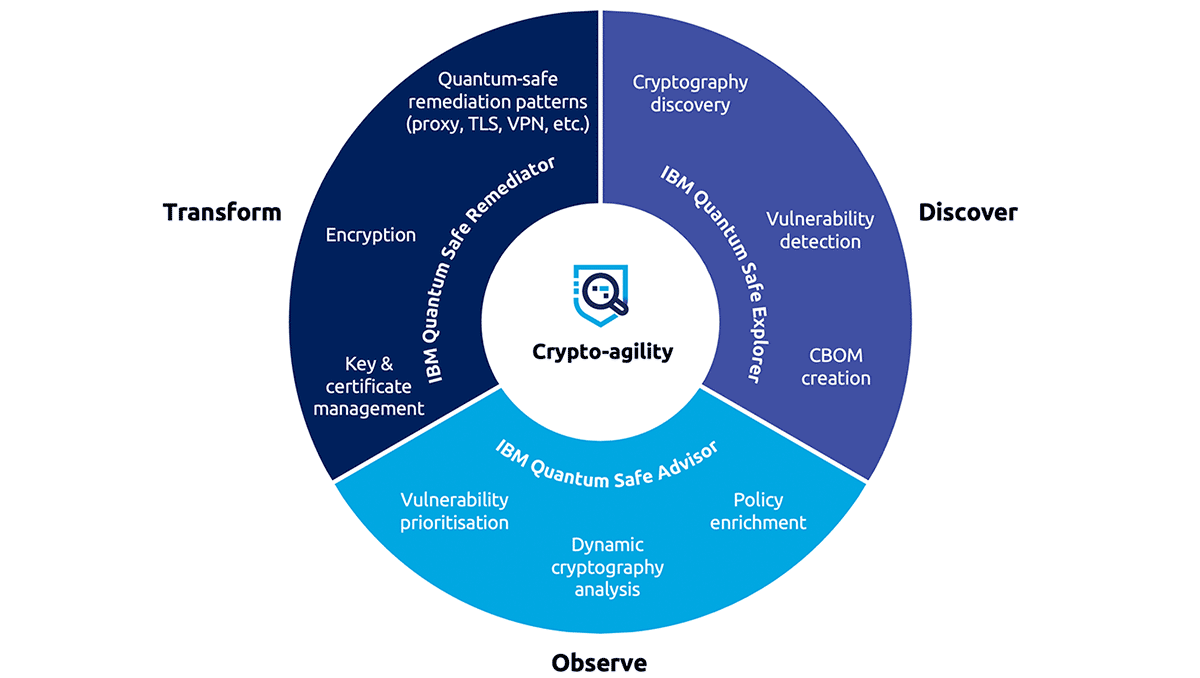
Figure 1. IBM Quantum Safe Technology approach
Cybersecurity and data protection guidelines
There are multiple existing cybersecurity risk management guidelines and frameworks that have been widely adopted by organisations, such as the following:
-
NIST Special Publication 800-37: Risk Management Framework (RFM) for information systems and organisations: A system life cycle approach for security and privacy [RMF18].
-
NIST Cybersecurity Framework (CSF) for improving critical infrastructure cybersecurity [CSF18].
-
ISO/IEC 27001: Information security, cybersecurity and privacy protection – Information security management systems [ISO22a].
-
ISO/IEC 27005: Information security, cybersecurity and privacy protection – Guidance on managing information security risks [ISO22b].
These standards share a common focus on effective risk management in information security, emphasising a systematic approach to comprehensively identify, assess, and manage risks. They advocate continuous monitoring, assessment, and improvement to address evolving cybersecurity threats, considering technical aspects, governance, processes, and human factors.
In Singapore, the Personal Data Protection Act (PDPA) aims to protect individuals' personal data by establishing guidelines for its collection, use, and disclosure. Organisations must implement reasonable security arrangements to safeguard personal data from unauthorised access, disclosure, alteration, or destruction. Cryptography plays a crucial role in cybersecurity risk management in ensuring data confidentiality, integrity, and authenticity.
For example, encryption is used to secure data at rest, in transit, and during processing to mitigate the risk of data breaches and unauthorised disclosures, in alignment with PDPA requirements.
Despite their widespread adoption, current risk management frameworks lack provisions for quantum-safe security and reveal gaps that must be addressed. Consideration of quantum risks should be integrated into existing risk assessment processes. Organisations must focus on evaluating the longevity of the data that supports critical applications. For prolonged data protection, there is a pressing need to introduce additional mitigating controls. Quantum computing threats pose risks to sensitive health and financial data, compromise the confidentiality of communications, challenge the integrity of digital documents, and threaten cryptocurrencies.
The emergence of ‘harvest now, decrypt later’ tactics underscores the urgency for organisations to fortify their cybersecurity measures against quantum advancements. Proactive adjustments to risk management strategies are crucial to navigate evolving threats and ensure the resilience of information security frameworks in the face of quantum challenges.
Quantum risk assessment
In what follows, we give an overview of two examples of quantum risk assessment frameworks which have been published within the quantum-safe community: Mosca’s Quantum Risk Assessment (QRA) [MM23] and Crypto Agility Risk Assessment Framework (CARAF) [Ma21]. Moreover, we highlight the limitations of the frameworks.
Mosca’s QRA uses a time-based approach to define risk that is dependent on when migration to a quantum-safe state begins and considers ‘harvest now, decrypt later’ attacks. The methodology for the framework has been adapted from the six stages for conducting a risk assessment outlined in the NIST Cybersecurity Framework [CSF18].
Mosca’s ‘x, y, z’ quantum risk model focuses on the dimensions of the impact of quantum computing. The ‘x’ parameter represents the lifetime of assets (the number of years encryption must be secure). The ‘y’ parameter indicates the time required to migrate to a quantum-safe state (the number of years required to bring current IT infrastructure to a quantum-safe state). The ‘z’ parameter considers the time until current cyber defences collapse in the face of threat actors with access to quantum technology (the number of years before a large-scale quantum computer is built). Based on these parameters, organisations can assess the urgency and potential consequences of quantum threats as a guide for the development of strategic and timely responses that ensure the security of their cryptographic systems.
CARAF builds on Mosca's QRA by specifically addressing cryptographic agility. Cryptographic agility involves the swift replacement of vulnerable cryptographic primitives, algorithms, and protocols with more secure alternatives. The conventional process of transitioning from one cryptographic solution to another can be time-consuming and can potentially leave organisations exposed to security risks during the transition period.
The CARAF framework can be used to systematically analyse and assess the risks arising from the absence of cryptographic agility. By leveraging CARAF, organisations can thoroughly evaluate their cryptographic systems' agility, identify potential vulnerabilities, and assess the associated risks. This analysis can be used for the development of a mitigation strategy that aligns with the organisation’s risk tolerance. Essentially, CARAF provides a structured approach for organisations to navigate the challenges of crypto agility, enabling them to make informed decisions about their cryptographic infrastructure and security postures in the face of evolving threats and technological advancements. Further details on CARAF and Mosca’s QRA, and their comparison can be found in [FS-ISAC23a].
Cautionary notes: The methodology used for the Mosca framework often results in assigning a low-risk classification when ‘z’ representing the time to compromise, ranges from 15 to 20 years. This approach tends to prioritise items with extended security and expected useful life timeframes over high-impact areas that may not require a prolonged security useful life. The emphasis is placed on identifying sensitive or critical data that could be vulnerable to future threats, including scenarios such as a ‘store now and decrypt later’ attack. The risk determination process categorises assets as either ‘at risk’ or ‘not at risk’ without considering nuanced risk levels for effective prioritisation. This means that assets with significant impact, such as the telecommunication control plane, may have lower ‘x’ or ‘y’ values but should not be categorised as having low, or no risk, and points to the need for more nuanced risk assessment [GSMA23].
Perspectives on quantum risk management
In 2016, the National Institute of Standards and Technology (NIST) projected that a quantum computer capable of breaking 2000-bit RSA encryption could be built by 2030 for about a billion dollars [Chen16]. However, various research institutes and technology firms have offered different timelines that range from less than 10 to up to 30 years. A reliance on speculative quantum timelines for risk assessment could potentially lead organisations to adopt a passive ‘wait-and-see’ approach. Organisations run the risk of being caught off guard, or left with insufficient time to take mitigation measures, if there is a breakthrough in the advancement of quantum computing in the near future. This risk increases if there is a new discovery, or design flaws, in the current crypto systems running in existing environments.
Our suggested approach moves away from relying on a specific quantum timeline and instead focuses on strengthening the overall cybersecurity risk management framework. Rather than adopting an entirely new framework, quantum risk management should be integrated into existing cybersecurity practices. The process should be continuous and adaptable based on dynamic threats, emerging vulnerabilities, and evolving regulatory environments. With an eye toward the need for the constant vigilance and adaptability that an ever-changing cybersecurity environment requires, key factors for managing quantum risk within an organisation are outlined below:
Get the basics right
Addressing the quantum threat requires that organisations proactively assess their readiness and understand both known challenges and potential unknown implications. The first step involves cataloguing all instances of cryptography usage which will include encryption keys, algorithms, applications, and their associated business processes. This comprehensive inventory will empower organisations to achieve crypto agility and enable strategic planning and adaptability in the evolving quantum-safe security landscape.
Effective monitoring of potential impacts requires careful consideration and the maintenance of critical elements. At a minimum, these elements should encompass the following aspects[FS-ISAC23a]:
-
Applications: Organisations should assess both in-house and vendor applications, examining their utilisation of cryptographic algorithms. An inventory of critical and high-availability applications, along with an overview of internal and external application connections, is vital for a thorough understanding of the cryptographic landscape.
-
Third-party vendors: Evaluate vendor roadmaps to ascertain their support for post-quantum cryptography. Procurement considerations should align with the organisation’s commitment to PQC to ensure that vendors comply with evolving security standards.
-
Data: It is crucial for organisations to determine the duration required for data asset protection. Classifying datasets based on sensitivity and criticality aids in developing a targeted security strategy. Additionally, organisations must assess the risk of a ‘harvest now, decrypt later’ attack scenario, especially for highly sensitive information.
-
Regulations: Organisations should be prepared to respond to potential queries from regulators regarding compliance with industry standards and guidelines. Addressing questions promptly and transparently is essential to maintaining regulatory compliance.
-
Location of data: Data residency introduces a layer of complexity, as different jurisdictions may have varying timelines for adopting post-quantum cryptographic measures. Organisations must align their strategies with regional timelines to ensure a cohesive and effective implementation of security measures. By systematically addressing these considerations, organisations can proactively navigate the challenges posed by the evolving quantum threat landscape.
Start small, start now
According to the World Economic Forum’s Global Future Council on Quantum Computing, a staggering 20 billion digital devices are projected to require upgrading or replacement with PQC within the next two decades [WEF20]. Based on the scale of the required transition, it will not be a mere switch-out or patch. PQC will profoundly transform numerous devices and systems including ATMs, TV set-top boxes, smartphones, and many more. Algorithm replacement, a key aspect of transition, is disruptive and often requires years to complete. There is an urgent need for organisations to plan for, and adopt, a posture of crypto agility.
Commencing this transformative journey is not just recommended – it’s a strategic imperative. Organisations are advised to adopt a pragmatic and phased approach, with key plans and objectives serving as a foundational framework for the migration process:
-
Identify critical business processes: Identify key processes that are heavily reliant on critical data to understand specific areas demanding immediate attention.
-
Conduct comprehensive risk assessment: Undertake a thorough risk assessment against critical business processes to evaluate vulnerabilities and potential threats for the creation of a risk register for structured mitigation.
-
Establish risk tolerance and crypto agility: Define risk tolerance levels and embrace crypto agility principles, prioritising remediation efforts based on asset value or risk. Understand quantum technology capabilities and challenges, assessing the business impact of quantum computing advancements for informed decision-making in the quantum era.
A phased approach enables gradual adaptation, a focus on higher-value or higher-risk assets, and strategic alignment with the evolving quantum technology landscape.
Continuous learning and monitoring
Following the identification of cryptography uses for key business processes, and an initial risk assessment, organisations must adopt a vigilant and adaptive strategy that addresses expected quantum-resistant security challenges. Continuous development and monitoring are imperative:
-
Monitor quantum computing development: Stay informed about ongoing developments, breakthroughs, and potential quantum applications that could impact existing cryptographic systems.
-
Understand vulnerabilities in crypto systems: Develop a comprehensive understanding of both known and emerging cryptographic vulnerabilities associated with quantum threats through continuous research and awareness initiatives.
-
Adhere to standards and regulatory requirements: Align with the emerging standards and regulatory requirements set by national cybersecurity institutions, such as the three new PQC standards recently announced by NIST [NIST04].
-
Evaluate vendor readiness: Assess the readiness of third-party vendors and solution providers in the quantum realm, including technologies based on PQC, quantum key distribution (QKD), and quantum random number generators (QRNG).
-
Enhance crypto agility: Strive to efficiently update cryptographic algorithms, parameters, processes, and technologies to respond adeptly to new protocols, standards, and security threats posed by quantum computing. Consider factors such as data and cryptographic assets, cryptographic keys, and infrastructure limitations.
Furthermore, organisations should consider hybrid solutions that integrate classical and quantum-ready approaches. This strategic approach overlays existing security measures with robust post-quantum cryptography algorithms, providing assurance during the transition to quantum-safe security.
By adopting these ongoing measures, organisations can establish a resilient posture in the face of quantum computing advancements. This continuous development and monitoring strategy will fortify cryptographic systems and enable organisations to navigate the complexities of the evolving quantum landscape with agility and preparedness.
Next steps
Forward-leaning companies and governments are preparing for a quantum computing future and positioning themselves to capture the many benefits of this technology. Yet, more can and should be done, and collaboration is needed. Governments, researchers, academics, and industries will need to work together on policies to accelerate the adoption of new educational curricula, fund research and development, and create new talent pipelines.
Migrating to quantum-safe security requires a multi-pronged approach that combines proactive action, strategic planning, and continuous adaptation. In what follows, we summarise key next steps and considerations:
-
Inventory & assessment: Start by identifying all assets and systems that rely on cryptography, especially those using vulnerable algorithms such as RSA and ECC. Prioritise assets based on their importance and the sensitivity of the data that they handle. Evaluate how the adoption of quantum-resistant algorithms might impact their performance and compatibility.
-
Pilots & testing: Engage in pilot projects to test chosen PQC solutions in real-world scenarios. Assess the impact of PQC solutions on performance, check for compatibility issues, and identify potential integration challenges. Gather valuable data and feedback from these pilot projects to refine and enhance the overall migration strategy for the future.
-
Planning & strategy: Develop a comprehensive migration strategy for adopting PQC algorithms. Evaluate and select PQC algorithms that align with specific security needs and requirements. Prioritise systems holding high-value data and critical infrastructure. Factor in costs, resources, and training considerations for each phase of the migration.
-
Deployment & rollout: Implement PQC solutions in a phased manner, starting with high-risk or critical systems and data. Establish robust key management and lifecycle practices specifically designed for PQC keys to ensure their secure and effective use.
-
Awareness & training: Educate employees on the risks associated with quantum computing and emphasise the necessity for migration to quantum-safe systems. Provide training to equip teams with the knowledge and skills required to securely use and manage quantum-safe systems. Foster a culture of cybersecurity awareness and vigilance across the organisation.
-
Monitoring & maintenance: Continuously monitor implemented PQC solutions for vulnerabilities and performance. Stay informed about the evolving quantum threat landscape and adapt security measures. Keep a close eye on standardisation efforts by organisations such as NIST and ETSI
The IBM-NCS value proposition
Why an IBM-NCS partnership?
The partnership between IBM and NCS is driven by the shared commitment to ensure quantum-safe security for organisations in Singapore and beyond. IBM, a global leader in quantum computing development, has not only been at the forefront of quantum technology but has also played a crucial role in creating quantum-safe technologies that were showcased in the NIST post-quantum cryptography competition. Three of the four technology finalists in that competition were developed by IBM in collaboration with industry and academic partners.
NCS stands out as a prominent digital and technology service provider in the Asia Pacific region and is particularly known for its role as a trusted system integrator for government agencies in Singapore over the past four decades. With a strong track record in successfully executing large-scale projects, NCS Cyber complements NCS’ core capabilities in applications, engineering, and infrastructure with security solutions and services. This collaboration allows NCS to leverage IBM's expertise in quantum-safe security, ensuring that clients receive top-notch consultancy services.
The IBM-NCS partnership offers more than just advanced security solutions. We bring practical benefits to your business, such as ensuring compliance, gaining competitive advantage, and building customer trust in the era of quantum computing.
Recognising the profound impact quantum-safe security will have on both legacy systems and new deployments dealing with sensitive data, NCS and IBM aim to prepare clients for a quantum-safe future through our combined knowledge and experience.
Specialised domain knowledge and capabilities
The collaboration between NCS and IBM brings together a wealth of specialised resources, including Ph.D.-trained personnel, qualified consultants, and skilled engineers. These resources each possess in-depth knowledge of the evolving quantum-safe technology landscape. This expertise spans the intricacies of cryptographic algorithms, their applications, and the systems and infrastructure where these algorithms find deployment.
This partnership transcends the conventional supplier-client relationship by offering more than just technology solutions. It extends to delivering comprehensive packages that encompass expert advisory services, processes, and experiences. Clients stand to benefit not only from cutting-edge technological advancements, but also from the collective expertise and proficiency of a team that is well-versed in navigating the complexities of quantum-safe implementations. As a result, the IBM-NCS collaboration ensures a holistic approach to addressing the challenges posed by quantum threats.
Localisation
NCS has a profound understanding of prevalent cybersecurity risk management and data protection frameworks that allows us to intricately navigate the guidelines and best practices stipulated by local authorities. We have a comprehensive knowledge of, and experience with, regulatory standards such as the Personal Data Protection Act (PDPA), IM8, CCoP 2.0, as well as sector-specific guidelines for the banking and healthcare industries. By leveraging this extensive expertise, NCS and IBM are uniquely positioned to align with local requirements in the realm of quantum risk assessment and management. The joint offerings of the partnership are designed to complement existing risk assessment frameworks and ensure a seamless integration that addresses the specific needs and intricacies of the local regulatory landscape. This approach underscores our commitment to delivering quantum-safe solutions that not only meet global standards but also resonate with the nuanced requirements of the communities they serve.
References
1 https://www3.weforum.org/docs/WEF_Quantum_Readiness_Toolkit_2023.pdf
[WEF23] Quantum Readiness Toolkit: Building a Quantum-secure Economy. World Economic Forum, Jun 2023.
[Ma21] C. Ma et. al., CARAF: Crypto Agility Risk Assessment Framework, Journal of Cybersecurity, pages 1-11, 2021.
[MM23] M. Mosca and J. Mulholland, A Methodology for Quantum Risk
Assessment. Global Risk Institute, 2023.
[Chen16] L. Chen et. al., Report on Post-quantum Cryptography, Vol. 12. US Department of Commerce, National Institute of Standards and Technology, 2016.
[GSMA23] GSMA, Guidelines for Quantum Risk Management for Telco version 1.0, 22 September 2023.
[RMF18] NIST Special Publication 800-37 - Risk Management Framework (RFM) for Information Systems and Organisations A System Life Cycle Approach for Security and Privacy, Revision 2, December 2018.
[CSF18] NIST Cybersecurity Framework (CSF): Framework for Improving Critical Infrastructure Cybersecurity version 1.1, April 2018.
[KM20] NIST Special Publication 800-57 - Recommendation for Key Management: Part 1 - General. Revision 5, May 2020.
[ISO22a] ISO/IEC 27001: Information Security, Cybersecurity and Privacy Protection – Information Security Management Systems, 2022.
[ISO22b] ISO/IEC 27005: Information Security, Cybersecurity and Privacy Protection – Guidance on Managing Information Security Risks, 2022.
[FS-ISAC23a] FS-ISAC: Risk Model Technical Paper, Post-quantum Cryptography (PQC) Working Group, 2023.
[WEF20] WEF: Global Future Council on Quantum Computing, June 2020. https:// www3.weforum.org/docs/WEF_Global_Future_Council_on_Quantum_Computing.pdf.
[NIST24] NIST Releases First 3 Finalised Post-quantum Encryption Standards, August 2024. https://www.nist.gov/news-events/news/2024/08/nist-releases-first-3-finalized-post-quantum-encryption-standards.