Published: Jan 15, 2025
Key questions to maintain and expand digital trust
securing digital transformation
Digital Trust is a necessity in a world where digital technologies support and intermediate virtually all economic transactions, social connections, and institutions. It is the expectation of individuals that digital technologies and services, and the organisations providing them, will protect all stakeholder interests and uphold societal expectations and values [WEF22]
The core of Digital Trust is the notion that we need to safeguard:
- Data
- Artificial Intelligence (AI)
- Digital identity, and
- Systems and infrastructure
There are already well-established and mature cybersecurity solutions for securing systems and infrastructure, including firewalls and software for network intrusion detection and prevention, malware analysis and detection, and vulnerability scanning. In this paper, we will focus on what we believe will be crucial to delivering trustworthy digital technologies and services going forward.
In the realm of Digital Trust, three critical security aspects stand out from traditional cybersecurity paradigms. Each aspect addresses specific challenges inherent to the evolving digital landscape:
-
Digital identity management: In expansive digital domains such as the Metaverse, and within the context of cryptocurrencies in particular, the preservation of digital identity becomes paramount. Protecting individuals and organisations from impersonation and fraud is a multifaceted challenge. Innovative solutions, such as biometric authentication, decentralised identity frameworks, and blockchain technology, are crucial to establishing and safeguarding digital identities. The goal of digital identity management is to create robust systems that can reliably authenticate and verify the digital personas of users to ensure trust and security in virtual spaces.
-
Data privacy: As our transactions and data processing activities increasingly migrate to the cloud, ensuring the confidentiality of sensitive data, especially Personally Identifiable Information (PII), is imperative. Encryption, secure data transmission protocols, and robust access controls are integral to safeguarding data privacy. Additionally, compliance with data protection regulations, like GDPR, plays a pivotal role in establishing transparent and ethical data practices and fosters trust among users regarding the secure handling of their information in digital environments.
-
AI security: The rapid advancement of AI introduces a new and unique set of security challenges. Embedding security into AI systems is crucial to preventing malicious or unethical use. Adversarial attacks, biased algorithms, and unintended consequences are potential pitfalls. Implementing secure development practices, robust testing procedures, and ongoing monitoring is essential. Ethical considerations, explainability, and accountability frameworks are also vital in ensuring the responsible deployment of AI technologies. Collaborative efforts across industries and interdisciplinary approaches are necessary to stay ahead of evolving threats in the AI landscape.
To address these aspects of Digital Trust, a holistic and proactive approach is essential. The convergence of technological innovations, regulatory frameworks, and ethical considerations forms the foundation for building resilient, secure, and trustworthy digital ecosystems.
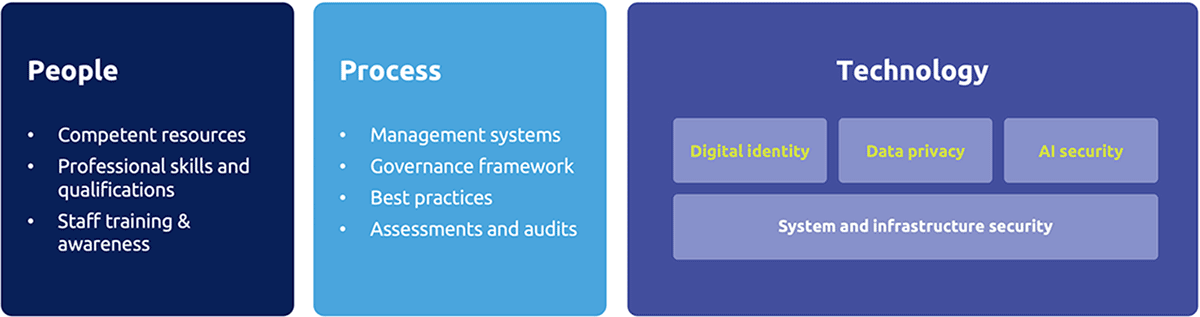
Figure 1: Building blocks of Digital Trust
That said, in building a trustworthy digital economy and society, it is crucial to recognise that technology alone is insufficient. As illustrated in Figure 1, consideration must extend to the people and process aspects when operationalising Digital Trust.
People
-
Competent resources: Developing Digital Trust requires a workforce equipped with the necessary professional skillsets and qualifications. Competent resources ensure the effective implementation and management of a variety of emerging technologies that are critical for building and maintaining trust.
-
Continuous staff upskilling and training: The dynamic nature of technology requires a workforce that is adaptable and continuously upskilled. Regular training programmes are essential to keep employees abreast of the latest developments, security threats, and best practices, ensuring that they can effectively contribute to Digital Trust initiatives.
-
Creating awareness: Organisations must foster awareness of the significance of Digital Trust within their workforces. This includes an understanding of the impact of employee actions on cybersecurity and overall trustworthiness. Employee awareness campaigns contribute to a culture that values and prioritises Digital Trust.
Process
-
Management systems and governance frameworks: Establishing proper governance frameworks and management systems is crucial for guiding employees in executing digital transformation initiatives. These frameworks will provide a structured approach to decision-making, risk management, and compliance, ensuring that technology adoption is aligned with the goals of Digital Trust.
-
Regular assessments and audits: To identify and rectify potential risks or gaps associated with cybersecurity and Digital Trust, organisations should conduct regular assessments and audits. These evaluations will help in proactively addressing vulnerabilities, enhancing security measures, and maintaining the integrity of digital systems.
In summary, people and process elements are integral components of a strategy to cultivate Digital Trust. By investing in competent resources, fostering continuous upskilling, creating awareness, and implementing robust governance frameworks and assessment procedures, organisations can fortify their digital ecosystems and create trust among users and stakeholders.
In the remainder of this article, we will investigate a set of questions that should be asked by organisations in their digital transformation journeys. The questions and their associated Digital Trust elements are summarised in the table below.
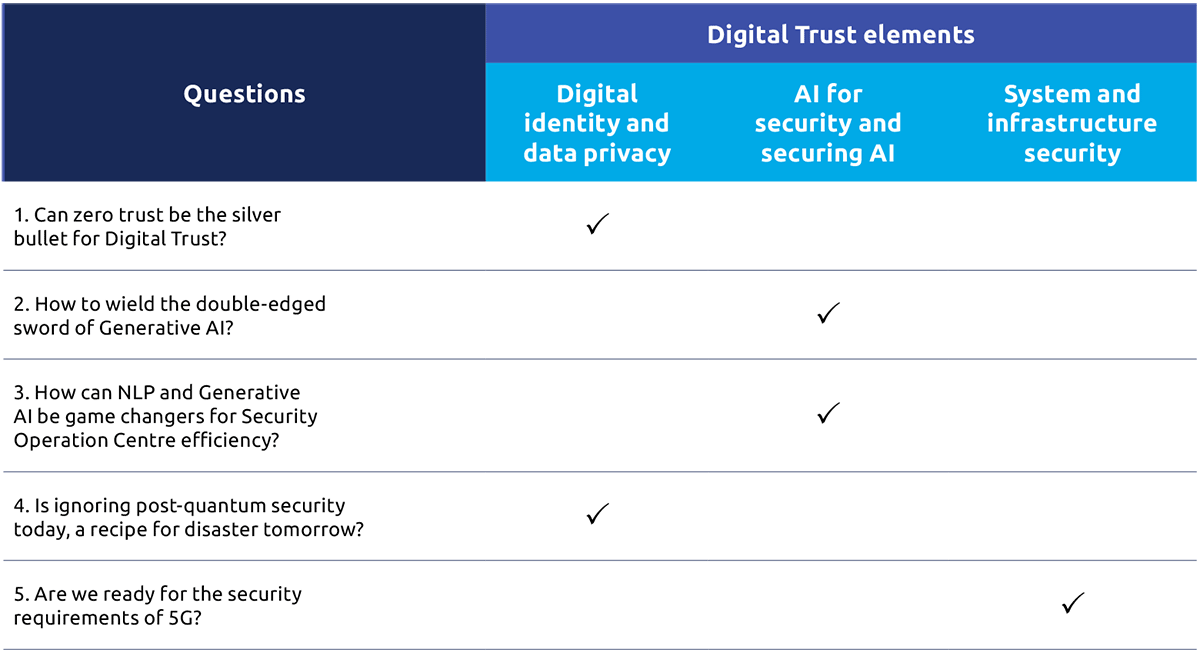
Table 1 : Mapping from Ask the Right Questions to Digital Trust elements
Q1: Can zero trust be the silver bullet for Digital Trust?
Interest in zero trust security has been largely driven by government mandates, vendor hype, ransomware attacks, and the needs of a hybrid workforce. According to Gartner, over 60% of organisations will embrace zero trust as a starting point for their cybersecurity strategies by 2025 [WDKW22].
Key value of zero trust
Prevailing IT security architectures depend on ‘implicit trust,’ which is granted once certain criteria are met, such as when a user is inside a corporate network. This is a vulnerability that demands remediation to prevent excessive access, as users have relatively unrestricted access to resources once inside the network under implicit trust protocols. The zero trust model dismantles implicit trust, ushering in a paradigm where trust is continuously assessed, explicitly calculated, and dynamically adaptive, contingent on identity and context. This model serves as a guiding principle for security strategies that not only define the architectural landscape but also enhance security posture and fortify cyber resilience. Organisations embracing the zero trust mindset and architecture stand to gain two pivotal technical outcomes:
-
Resilient infrastructure: Zero trust principles significantly bolster the resiliency of IT infrastructures. A zero trust network, crafted to operate even in the presence of adversaries, excels at containing and managing incidents. This proactive approach diminishes the likelihood of business-impacting events such as ransomware attacks, data compromises, and malware infections. The consequent reduction in risk that zero trust models provide, contributes to the overall robustness and security of the business.
-
Adaptive work environment: Modern work environments must be adaptable to accommodate the anticipated hybrid nature of work in the future. Zero trust principles seamlessly support remote workers’ use of both managed and unmanaged devices, remote data (e.g., IaaS), and remote applications (e.g., SaaS). A secure zero trust implementation enables the realisation of an "anywhere, any time, on any appropriate device" approach that will be crucial for supporting a dynamic and hybrid workforce.
From zero trust to Digital Trust
A zero trust approach can play a pivotal role in achieving overall Digital Trust by redefining traditional security paradigms, fortifying defences, and instilling confidence in users engaged in digital interactions. As digital transformation accelerates, the conventional approach of assuming trust is no longer tenable, prompting the need for a more sophisticated and proactive security model that emphasises continuous verification, explicit calculation, and adaptive trust based on identity and context. Here are some examples of how zero trust can enable Digital Trust:
-
Digital identity management: Digital identity is the cornerstone of secure online interactions. Zero trust challenges the conventional notion of trusting users and devices by default. Instead, it advocates continuous authentication and authorisation, ensuring that trust is earned and maintained throughout the digital journey. Zero trust models leverage multifactor authentication, biometrics, and contextual information to establish and validate identities. This meticulous scrutiny reduces the risk of unauthorised access, identity theft, and impersonation. By embracing zero trust principles in digital identity management, organisations enhance their ability to safeguard user identities across various platforms, including the Metaverse and cryptocurrency ecosystems. The continuous assessment of digital identities fosters confidence among users that their online personas are protected, thereby contributing to the establishment of Digital Trust.
-
Data privacy: Zero trust can be extended to data privacy, which is a critical concern in an era marked by cloud-based transactions and ubiquitous data processing. In a zero trust architecture, the default assumption is that no entity, whether internal or external, should be implicitly trusted. This approach is particularly relevant when transacting and processing sensitive data, including personally identifiable information. Implementing zero trust in data privacy involves encryption, secure data transmission protocols, and robust access controls. By assuming a position of continuous scrutiny, organisations employing zero trust frameworks are better equipped to detect and thwart potential data breaches. This not only enhances the confidentiality of sensitive information but also instils confidence among users that their data is being handled with the utmost care and security.
-
AI security: As the influence of AI grows, so does the need to secure AI systems from malicious exploitation. Zero trust principles are instrumental in embedding security into AI processes. The rapid evolution of AI technology introduces potential risks including adversarial attacks and unintended consequences. Zero trust in AI security involves integrating security measures into the development lifecycle of AI systems. This includes secure development practices, robust testing, and ongoing monitoring. Moreover, ethical considerations such as transparency, fairness, and accountability are integral to the responsible deployment of AI. By adopting a zero trust approach to AI security, organisations can mitigate the risks associated with the malicious use of AI, thereby reinforcing Digital Trust.
Where are we today?
The implementation of zero trust technologies marks a fundamental shift from traditional network security practices, and while the benefits are manifold in enhancing organisational security posture, the transition to zero trust is far from straightforward. It requires a meticulous rethinking of network design and access strategies, with several challenges that demand attention.
The implementation of a zero trust architecture often brings about considerable operational overhead expenses. This is the case because zero trust mandates the continuous verification of all users and devices trying to access the network, regardless of whether they are inside or outside the organisation’s perimeters. For example, an organisation may need to frequently update and monitor access policies to ensure that they accurately reflect the current threat landscape and access needs, a process that can be both time-consuming and labour-intensive.
Furthermore, extending zero trust principles to legacy systems presents a unique set of complications. Older systems were not designed with zero trust in mind, and many lack the necessary interfaces to support modern authentication and authorisation protocols. A typical example can be found in manufacturing firms, where legacy industrial control systems, essential for day-to-day operations, may not support the latest security protocols. Retrofitting these systems to align with zero trust principles can be a resource-intensive task that requires both innovative technical solutions and substantial investment.
Another critical challenge is the scarcity of resources with the requisite skillsets. Zero trust is a relatively new and evolving concept, and there is a limited pool of professionals that has extensive experience in implementing such frameworks. For example, an organisation may struggle to find IT professionals who are adept at configuring the sophisticated access control policies required by a zero trust architecture, or who have the expertise required to manage the sophisticated network segmentation strategies it entails.
In summary, while the zero trust model offers a robust framework for securing modern digital assets, the path to its successful implementation is laden with operational, technical, and human resource hurdles. Addressing these challenges requires a well-structured approach, investment in the right technology, and most importantly, the cultivation of a skilled workforce capable of navigating the complexities of zero trust implementation. It is a complex journey, but one that can lead to a significantly more secure IT environment for organisations willing to make the commitment.
Q2: Taming the machine: How to govern AI for good?
AI security is a key enabler of Digital Trust as AI-supported applications and services are becoming pervasive. AI governance, in turn, sets the foundation, including the overall culture and structure for managing AI risk within an organisation to ensure ethical, lawful, and reliable use of AI in a manner that earns public trust.
Generative AI (GenAI) can be used to create a wide variety of content including text, code, images, and videos. This content can be used with good or malicious intent, so it is important to have safeguards in place to prevent GenAI from being used for malicious purposes.
To address the ethical and societal concerns surrounding AI (including GenAI), it is essential to develop and operationalise effective organisational governance frameworks. These frameworks should be designed to ensure that AI is used in a responsible and ethical manner.
Some of the overarching principles of effective AI governance include:
- Transparency: AI systems should be designed in a way that is transparent and accountable. This means that it should be possible to understand how these systems work and to identify the biases that they may contain.
- Fairness: AI systems should be designed in a way that is fair and does not discriminate against any particular group of people. This means that AI systems should be trained on datasets that are representative of the population and that they should be used in a way that does not perpetuate existing biases.
- Accountability: There should be clear lines of accountability for the development and use of AI systems, and it should be made clear who is responsible for ensuring that these systems are used in a responsible and ethical manner.
- Safety: AI systems should be designed in a way that is safe and does not pose a risk to human safety or security. This means that AI systems should be tested for potential vulnerabilities and that they should be equipped with safeguards to prevent misuse.
- Privacy: AI systems should respect user privacy and should not collect or use any personal data without a user's consent.
Once we have defined our overarching AI principles, we need to develop a governance framework that sets out how these principles will be put into practice. This framework should include policies and procedures for the development, deployment, monitoring, and evaluation of AI systems.
With the rise of GenAI tools such as ChatGPT, some recommended practices that organisations should adopt to ensure a responsible approach to AI include (using ChatGPT as an example):
-
Approve only a certain set of use cases: Decide which use cases for ChatGPT are acceptable and which ones are not. For example, organisations might want to allow ChatGPT to be used to generate personalised learning materials for students, but not to create fake news articles or deepfakes.
-
Avoid usage of certain input data: ChatGPT was trained on a massive dataset of text and code which could have contained personal information, confidential data, or biased content. It is important to avoid using ChatGPT to process any type of data that is sensitive or that could be used to harm or discriminate against individuals or groups.
-
Verify the accuracy of output from ChatGPT: ChatGPT is a powerful language model, but it is not perfect. It is important to verify the accuracy of any output from ChatGPT before using it. This is especially important for high-stakes applications such as ChatGPT use for medical diagnosis or legal decision-making.
-
Consider legal issues: When using ChatGPT, it is important to be aware of the relevant laws and regulations. For example, organisations need to ensure that they are not violating any privacy laws when collecting or processing data and that they are not infringing on any copyrights when generating content.
In addition to these recommendations, it is also important to be transparent about how ChatGPT is used. Users need to know what data is being collected, how it is being used, and what they can expect from the output of the model. It is also important to have a process in place for users to report any problems or concerns they have about the use of ChatGPT. By taking these steps, organisations will go a long way in ensuring that ChatGPT is used in a responsible and ethical way.
For further details, the U.S. National Institute of Standards and Technology (NIST) AI Risk Management Framework (AI RMF) serves as a comprehensive resource for organisations of all sizes, to manage AI risks effectively and to promote both trust and the responsible use of AI technology [AI-RMF23]. Figure 2 summarises the core functions of the NIST AI RMF:

Figure 2: Core functions of the NIST AI Risk Management Framework
Q3: Can NLP and Generative AI be game changers for Security Operation Centre efficiency?
In today's digital landscape, where Digital Trust is at stake and cyber threats are increasingly sophisticated, organisations must prioritise robust security measures to protect their assets, data, and reputations. Security monitoring solutions play a crucial role through the continuous surveillance and analysis of an organisation's security posture to detect, respond to, and mitigate potential threats in real time. A Security Operations Centre (SOC) serves as the ‘command centre’ for these activities, ensuring that organisations can effectively manage and mitigate cyber risks.
However, the operational challenges that come with running an efficient SOC can be daunting. As an example, the effort required to process and review large volumes of security alerts can lead to ‘alert fatigue’ among SOC analysts that can potentially result in cybersecurity attacks that aren’t detected. The integration of GenAI and NLP holds the potential to be 'game changing' for SOC efficiency.
It is important to understand the current role of NLP in SOC operations, and the differences between NLP and GenAI, before explaining how the combination of the two can improve both SOC efficiency and the security posture of an organisation.
NLP for Security Operations Centre (SOC) use cases
Natural Language Processing (NLP) plays a significant role in enhancing cybersecurity monitoring and threat detection by enabling machines to understand, interpret, and respond to human language. Here are five examples of how NLP can be useful:
-
Log analysis and anomaly detection: NLP can be used to analyse logs and security events to extract meaningful information from unstructured log data. By understanding natural language patterns in logs, NLP algorithms can identify anomalies or potential security incidents that may go unnoticed through traditional detection methods.
-
Threat intelligence and incident monitoring: NLP can be applied to process and analyse threat intelligence feeds, security blogs, news articles, and social media to identify emerging threats and vulnerabilities. Security teams can stay informed about the latest cyber threats by using NLP to extract relevant information and perform sentiment analysis.
-
Phishing detection and email security: NLP can enhance email security by analysing the content of emails and identifying phishing attempts. It can detect suspicious language, unusual patterns, or social engineering techniques, helping to filter out malicious emails and protect users from phishing attacks.
-
Incident response and chatbot security assistants: NLP-powered chatbots can provide immediate assistance during security incidents. Users can interact with a chatbot in natural language to report incidents, ask security-related questions, or receive guidance on security best practices. Use of NLP chatbots will enhance incident response capabilities and help improve communication between security teams and end-users.
-
User behaviour analytics and insider threat detection: NLP can be used to analyse user behaviour patterns in communication channels such as email, chat logs, and collaboration platforms. With their ability to understand natural language context, NLP algorithms can detect anomalies in user behaviour that may indicate insider threats, unauthorised access, or compromised accounts.
These examples illustrate how leveraging NLP for cybersecurity monitoring and threat detection enables a more sophisticated and context-aware approach to identifying and responding to security incidents. NLP enhances the capabilities of security systems by processing and understanding human language, thereby improving the overall effectiveness of cybersecurity measures.
While NLP offers valuable capabilities for cybersecurity monitoring, it also comes with certain limitations:
-
Evading linguistic analysis: Sophisticated attackers can intentionally craft messages to evade linguistic analysis. They may use obfuscation techniques, encryption, or slang to communicate without triggering NLP-based threat detection. This makes it difficult for NLP systems to consistently identify and interpret malicious communications.
-
Limited support for unstructured data: NLP is more effective for analysing structured data than unstructured data. While it can analyse textual content, much of the relevant cybersecurity information exists in unstructured forms such as log files, network traffic, and system events. Extracting actionable insights from these unstructured sources poses challenges for NLP.
-
Dependency on quality and quantity of training data: The effectiveness of NLP models depends heavily on the quality and quantity of training data. If the training data is not representative of the diverse language used in cybersecurity contexts, the model may struggle to accurately identify threats. Additionally, biases present in the training data may be perpetuated in the model's outputs.
-
Handling new and evolving threats: NLP models may struggle to adapt quickly to new and evolving cyber threats. Traditional rule-based systems may be more adept at handling novel attack methods, as NLP models often require retraining with new data to effectively detect emerging threats. The lag in adaptation can pose a significant limitation in fast-paced and dynamic cybersecurity environments.
While NLP provides valuable insights, it should be complemented with other technologies and methodologies to create a comprehensive and resilient cybersecurity strategy.
Generative AI vs NLP
Neither Generative AI (GenAI) nor NLP is inherently superior or inferior to the other, but rather, they serve different purposes and can complement each other across applications. Both are valuable technologies, and their strengths lie in different domains.
GenAI excels at creating new content, whether that be text, images, or other forms of data. It can generate realistic and contextually relevant content based on patterns it has learned during training. It is often used for content creation, creative tasks, text generation, and the simulation of diverse data scenarios. In contrast, NLP focuses on understanding and processing natural language. It deals with tasks such as language understanding, sentiment analysis, text classification, and named entity recognition. It is widely used for applications such as chatbots, language translation, sentiment analysis, and information extraction from textual data.
GenAI, therefore, can be used to complement NLP in multiple aspects. For example:
-
Content augmentation: GenAI can be used to generate diverse and synthetic data, which can be used to augment training datasets for NLP models. This will help improve the robustness and generalisation of NLP systems.
-
Simulating real-world scenarios: Generative models can simulate realistic scenarios, including cyber threats, which can be valuable for training and testing NLP-based threat detection systems. This can be especially useful when real-world threat data may be limited due to privacy concerns.
-
Enhancing training data quality: By generating additional data instances, GenAI can be used to overcome limitations in training data quality by generating additional data instances that provide added context and diversity to NLP models.
-
Addressing data privacy concerns: Generative models can generate synthetic content without relying on real incident data which helps address the privacy concerns associated with using actual threat data for training NLP models.
-
Improving response to new threats: GenAI can be employed to simulate new and evolving cyber threats, allowing security teams to proactively prepare for, and detect, emerging threats. This complements the reactive nature of NLP-based threat detection.
Enhancement to SOC capabilities
Combining GenAI and NLP can significantly enhance the capabilities of an SOC by providing a more comprehensive and adaptive approach to cybersecurity. This can be summarised as follows:
-
Threat intelligence augmentation: GenAI can create synthetic threat scenarios to simulate diverse and evolving attack vectors. NLP processes and understands threat intelligence feeds and extracts relevant information about known vulnerabilities, tactics, techniques, and procedures (TTPs). By integrating the synthetic scenarios from GenAI with the understanding of real-world threats NLP brings, SOC teams gain a more enriched and dynamic threat intelligence dataset. This will aid in proactive threat detection and incident response.
-
Automated incident response planning: GenAI can simulate incident response scenarios and create synthetic incidents for training purposes. NLP can be used to understand and process incident reports and to automate the extraction of relevant information. The SOC can leverage GenAI for realistic incident simulations and use NLP to automatically extract insights from incident reports to streamline incident response planning and execution.
-
Contextual understanding of security events: NLP analyses logs, alerts, and security event descriptions to understand the context of security incidents. GenAI can generate additional context for security events by simulating potential attack scenarios. The SOC gains a deeper understanding of security events from both NLP linguistic analysis and GenAI contextual enrichment. This will improve the accuracy of threat detection and reduce the number of false positives. These capabilities can also enhance the speed and efficiency of incident and management reporting for the SOC team.
-
Dynamic threat detection and adaptation: GenAI continuously adapts the scenarios it generates based on evolving threats. NLP processes real-time security information, identifying new threats and vulnerabilities. The SOC benefits from a dynamic and adaptive threat detection system that uses GenAI for scenario simulation and NLP for real-time analysis to improve its readiness for emerging threats.
-
User awareness and training: GenAI can create synthetic phishing scenarios for user awareness training. NLP can be used to process user feedback and identify common issues related to security awareness. By combining GenAI training scenarios with NLP-driven user feedback analysis, SOC teams can develop user awareness programmes that are more targeted and effective for addressing security vulnerabilities.
By combining the creative content generation capabilities of GenAI with the language understanding features of NLP, a SOC team can create more adaptive, informed, and proactive defence strategies against evolving cyber threats. This collaborative approach can help improve incident response, threat detection, and user awareness and ultimately strengthen the overall cybersecurity posture of the organisation.
Q4: Is ignoring post-quantum security today a recipe for disaster tomorrow?
Quantum computing is a double-edged sword. While it has the potential to solve certain types of complex calculations, including optimisation problems and simulations of quantum systems, more efficiently than classical computational tools, it can also be exploited to break widely used encryption algorithms. Algorithms such as RSA and Elliptic Curve Cryptography (ECC), which form the basis of secure communication on the internet, rely on the difficulty of certain mathematical problems. Quantum algorithms, such as Shor's algorithm, have demonstrated the potential to efficiently solve these problems and pose a threat to the security of encrypted data. These current (and expected future) advances in quantum computing threaten to negate the protection required to maintain Digital Trust. In particular, quantum computing poses significant threats to the three pillars of cybersecurity:
1. Authentication
-
Breaking cryptographic hash functions: Quantum computers can efficiently crack certain cryptographic hash functions, such as SHA-256, which are used for digital signatures and for verifying the identity of entities (e.g., websites, users). The use of quantum computers could compromise trust and security by allowing malicious actors to forge signatures and impersonate legitimate entities.
-
Man-in-the-middle attacks: With the ability to break encryption faster, quantum computers could make it easier to intercept and tamper with communication channels and allow attackers to steal authentication credentials or redirect traffic to fake websites.
2. Data integrity
-
Breaking digital signatures: Digital signatures rely on public-key cryptography and are used to verify that data has not been tampered with. Quantum computers could be used to break these algorithms, allowing attackers to modify data and make it appear unaltered, potentially leading to financial losses, the spread of misinformation, or even physical harm.
-
Manipulating timestamps: Quantum algorithms could be used to forge timestamps on digital documents, making it difficult to track data provenance and verify the authenticity of records. This could have implications for legal proceedings, financial transactions, and historical records.
3. Data confidentiality
-
Breaking encryption algorithms: Popular encryption algorithms, such as RSA and ECC, are vulnerable to quantum attacks. Attacks on encryption algorithms could lead to the decryption of sensitive data stored on computers or transmitted over the internet, including financial records, medical information, and personal data.
While quantum computers that pose a credible threat are still years away, the threat of “Harvest now and decrypt later” is a real, immediate, security risk that needs to be addressed today [FS-ISAC23]. This is a ‘long game’ attack where bad actors collect encrypted data, by way of breaches, or undertake passive interception and hoard the encrypted data, waiting for the day when quantum computers can decrypt that information. Therefore, it is imperative to start using quantum-resistant algorithms as soon as possible. Today, a bad actor can record, and store (harvest) encrypted data that is streaming through the internet or cloud, from a specific website, server, email client, or whichever target they deem worthy of attack. With enough resources, that bad actor could capture petabytes of data (or more) from general internet traffic.
The question of when cryptography will be broken by quantum computing is unfortunate, as it implicitly frames the threat to be some time in the future. The threat exists today, but the impact will become apparent in the future. Data that is considered securely protected today is already lost to a future quantum adversary if it has been stolen or harvested. All data—past, present, and future—that is not protected using quantum-safe security is at risk, and the longer we postpone the migration to quantum-safe standards, the more data there will be that is at risk.
Our experience makes it clear that there will not be a one-size-fits-all strategy when it comes to migrating to quantum-safe security. Given the long-term nature of the threat, and the dynamic environment surrounding quantum computing, it is also clear that a cryptographic strategy needs to consider multiple time frames and needs to consider potential step improvements in quantum technology development. To supplement the standards development underway by private industry players, governments need to accelerate their investment in quantum-safe cryptosystems and proactively promote the widespread adoption of the same.
The threat of cryptographically relevant quantum computers (CRQC) is significant, but the timeline for the materialisation of the threats they will enable is unknown. How can an organisation quantify the risk of cryptographically relevant quantum computers when they don’t yet exist? The immediate best practice suggests creating several scenarios of the risk a quantum threat poses to a specific asset, with some of these scenarios deemed as “more likely” than others.
The argument for starting to address the threat that quantum computers will pose to existing security systems now, is based on the following considerations:
-
Cryptographic technologies are integrated into most of the digital products commonly used by organisations to run their daily operations.
-
Some of the applications and systems currently used for energy, transportation, finance, and government infrastructure have expected product useful lives of 15 to 30 years, with longer requirements for data protection and privacy.
-
The time required to migrate installed cryptographic technologies (e.g., SHA1) to something newer is measured in years.
-
The number of cryptographic systems that organisations will need to migrate to use new “quantum-safe” cryptography will be large.
-
Most organisations have no clear view of the cryptographic technologies used in IT operations and this will make it difficult to discover, and then prioritise, the systems to be upgraded to post-quantum cryptography.
-
Migrating to quantum-safe security requires a multi-pronged approach that combines proactive action, strategic planning, and continuous adaptation. Table 1 summarises some key considerations.
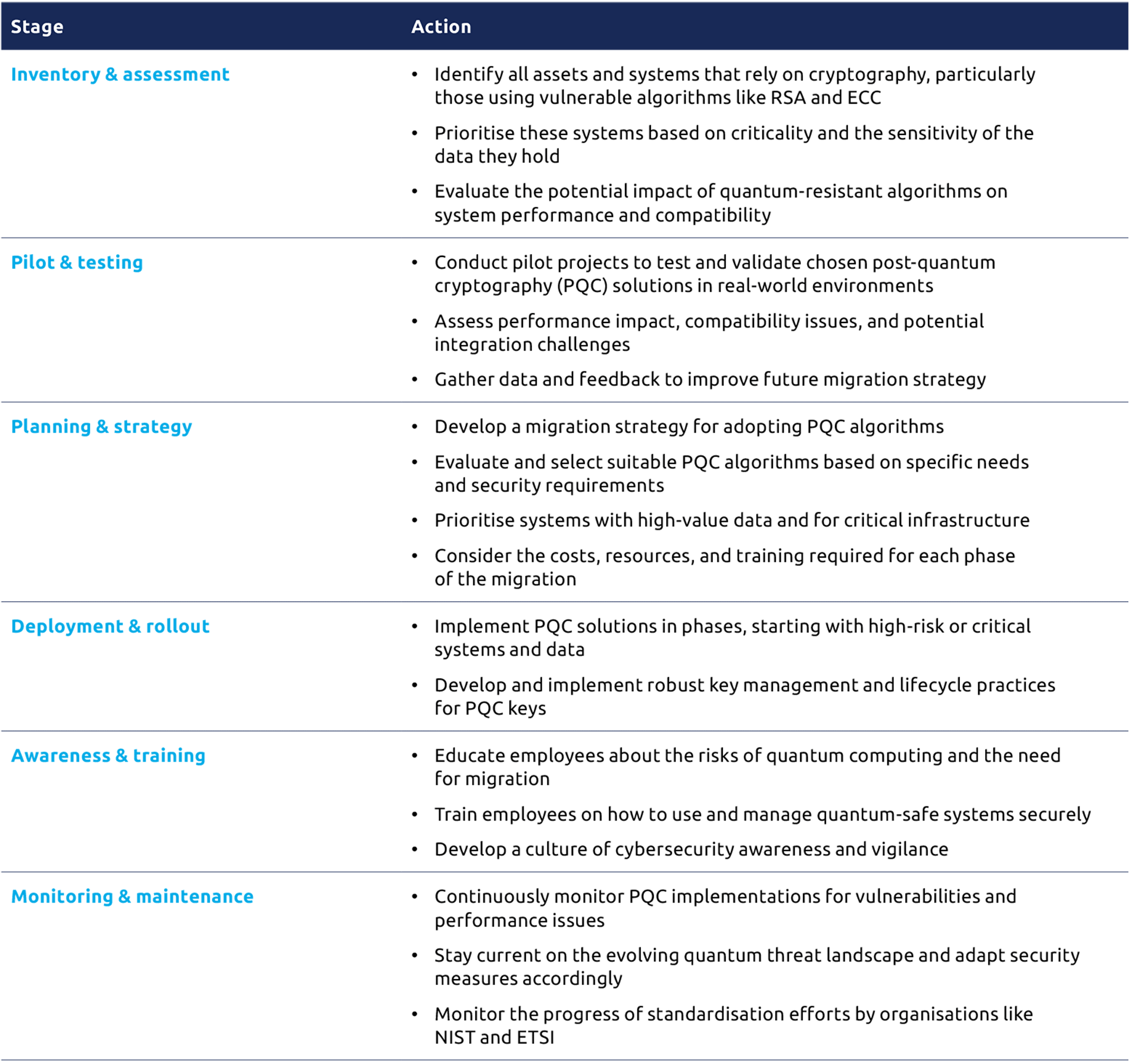
Table 2 : Recommended action plan for starting a quantum-safe journey
Migration to quantum-safe security is a continuous process and will take multiple years. It is important to stay adaptable, embrace new technologies, and adjust strategy as the landscape evolves. By taking proactive steps, and actively engaging with the community, we can ensure that our organisations are prepared for the challenges and opportunities of the quantum era.
Q5: Is the promise of 5G technology overshadowed by its security challenges?
While 5G technology promises transformative benefits like high-speed and low-latency communications, its global adoption has encountered challenges, leading to a slower rollout than initially anticipated. Key factors affecting the pace of rollout include the substantial infrastructure investments required for deployment, regulatory and spectrum allocation delays, and technological hurdles related to ensuring widespread coverage. Economic uncertainties, influenced by global events such as the COVID-19 pandemic, have also impacted investment priorities and consumer readiness, with the initial high cost and limited availability of 5G-enabled devices posing additional barriers. Furthermore, public health concerns, despite lacking scientific backing, have fuelled resistance in some areas. Nevertheless, as these challenges are progressively addressed—through regulatory adjustments, technological advancements, and increasing consumer device availability—5G adoption is expected to accelerate, unlocking its full potential for a wide range of applications and services.
The rollout of 5G technology brings transformative potential for connectivity, speed, and efficiency but also introduces several key security challenges. These challenges stem from the technology’s complexity, its extensive use of software, and the broad range of applications and services it aims to support. Key 5G security challenges include:
-
Increased attack surface: 5G networks utilise a more extensive and complex infrastructure in comparison to their predecessors, including the vast number of connected devices and new technologies such as network slicing and edge computing. This complexity significantly increases the attack surface, offering more opportunities for cyberattacks and making security management more challenging.
-
Supply chain security: 5G networks rely on a global supply chain that includes many vendors providing hardware, software, and services. Ensuring the security of this supply chain is crucial, as vulnerabilities or malicious insertions at any point can compromise the entire network. The risk is exacerbated by the potential for state-sponsored threats aimed at exploiting supply chain weaknesses for espionage or sabotage purposes.
-
Privacy concerns: The massive amount of data transmitted over 5G networks, combined with advanced technologies capable of processing this data at unprecedented speeds, raises significant privacy concerns. Protecting user data against unauthorised access, and ensuring compliance with data protection regulations, becomes increasingly complex in a 5G context.
-
End-to-end encryption challenges: While 5G promises enhanced security features, including improved encryption compared with earlier generations, implementing end-to-end encryption across the entire network and ensuring the confidentiality of data in transit remains a challenge. This is particularly the case for scenarios involving network slicing, where different slices may have varying security requirements and capabilities.
-
Dynamic network configuration and management: 5G networks enable dynamic network configuration and management to support a wide range of applications with differing performance requirements. This dynamic nature, while being a strength of 5G, complicates the security management of the network. Ensuring consistent security policies and effective incident response across an ever-changing network topology require sophisticated security tools and strategies.
Addressing these challenges is critical for ensuring the security and reliability of 5G networks. It requires a concerted effort from network operators, equipment manufacturers, service providers, and regulatory bodies to develop and implement robust security frameworks that can adapt to the evolving threat landscape associated with 5G technology.
With the ongoing rollout by Mobile Network Operators (MNOs), the Cyber Security Agency of Singapore (CSA) published the ‘Guidelines for CII (Critical information Infrastructure) Owners to Enhance Cyber Security for 5G Use Cases’ in April 2022. The guidelines outline possible cyber threats to systems connected to 5G services and provides recommendations to mitigate these risks. Here are five key security recommendations from the CSA guidelines:
-
User equipment assurance: CIIOs must ensure that user equipment connecting to 5G networks achieves high levels of security assurance. This includes maintaining valid security assurance certifications, such as those under CSA’s Cybersecurity Labelling Scheme (CLS) and keeping software/firmware updated to mitigate known vulnerabilities. Additionally, equipment nearing the end of its service life should be replaced to prevent network compromises.
-
Data protection: Protecting data from unauthorised access and corruption is paramount. CIIOs should implement encryption for data in transit across 5G networks. In scenarios where encryption may not be feasible, data integrity verification measures should be applied. Ideally, end-to-end encryption is recommended for all system communications. For data stored on user equipment (UE), secure industry-standard encryption algorithms should be used, with hardware-based root of trust modules (e.g., TPM) deployed to protect critical data.
-
Configuration management: The configuration of systems connected to 5G networks should be meticulously planned, documented, reviewed, and tested. Implementing technical solutions to document and maintain configurations can facilitate system recovery and prevent misconfigurations. CIIOs should ensure that UE, regardless of location or direct connection to the CII network, complies with the latest cybersecurity policies.
-
Access control: Access to the CII network should be strictly controlled based on the user’s credentials and the security posture of the UE. This encompasses implementing network access control, identity and access management, and interface authentication. Access control policies should be regularly reviewed, and multi-factor authentication is recommended for accessing UE or connecting to the CII network through 5G.
-
Monitoring of devices over the 5G network: Continuous monitoring of devices is essential for detecting abnormalities and security incidents. CIIOs should monitor both the operational status and physical location of UE to prevent unauthorised relocation. For devices that may not always be connected to the 5G network, such as IoT sensors, system operators should be alerted if the devices fail to connect after a predefined interval or in the event of unauthorised access.
However, 5G is a relatively new technology, and the technical solutions available to system owners—Critical Information Infrastructure Owners (CIIOs) and enterprises—to mitigate the associated cybersecurity risks of deployment, may not be sufficiently tested for effectiveness and performance. Specific details for some of the solutions, such as the encryption schemes to use, have either not been prescribed or are said to be dependent on the 5G use case.
To address the need for testing that details the impact of various cybersecurity solutions on the effectiveness and performance of user equipment within 5G networks, a study on 5G cybersecurity technical solutions was commissioned by CSA. The intent of the study was to provide CSA with information, across a variety of use cases, about how security solutions and measures should be implemented to adequately protect CIIOs’ systems without compromising the potential operational benefits of 5G. The findings of the 5G security study are shared in a follow-up article.
Unveiling the strategic advantages of NCS Cyber
NCS, a prominent digital and technology service provider in the APAC region, offers a comprehensive suite of end-to-end services and digital solutions that encompass applications, infrastructure, engineering, and cybersecurity. In the evolving digital landscape, ensuring robust cybersecurity is pivotal to safeguarding organisations at each layer of the technology stack.
-
Applications: NCS empowers businesses by boosting productivity through cutting-edge business application solutions. We put client needs at the core of the application development process when creating enterprise-grade applications using AI. These applications not only address organisational needs but also cater to market demands to increase business agility for clients.
-
Infrastructure: A modern, current, infrastructure is crucial to business competitiveness and overall performance. NCS facilitates the transformation of organisational infrastructure to allow businesses to innovate faster and to adopt data-driven business models. NCS builds secure and responsive infrastructure that is tailored to the digital enterprise to ensure competitiveness.
-
NCS NEXT: The NCS NEXT team develops innovative solutions and experiences that transform and propel communities forward. The NCS team of specialists, located throughout the APAC region, possesses expertise to build and customise first-class enterprise solutions. That expertise extends to cloud innovation with services to ensure secure and compliant migrations, FinOps mastery for client cloud frameworks, and data-driven business evolution and expansion. With innovative products and platforms, NCS provides the tools and emerging technologies to future-proof businesses.
-
Cybersecurity: The NCS approach to security involves combining global cybersecurity expertise with state-of-the-art technologies to safeguard businesses against evolving cyber threats. NCS helps businesses stay ahead of new threats by providing access to a global team of certified security experts who are expert in the latest cybersecurity technologies. Personal information security advisors collaborate with clients to design tailored IT security solutions that align with business needs and objectives.
NCS integrates cybersecurity technologies, solutions, and services at each layer of the software and hardware stacks. To ensure protection of critical business applications from potential threats and unauthorised access, NCS addresses vulnerabilities at the application layer by focusing on API and container security. At the infrastructure layer, NCS integrates cutting-edge cybersecurity technologies, such as Database Activity Monitoring (DAM), Data Loss Prevention (DLP), and Network Intrusion Detection System (NIDS). These technologies span edge devices, networks, and cloud platforms and enhance security measures to prevent data breaches, detect unauthorised database access, and identify network intrusions. Recognising the diverse needs of different industries, NCS emphasises the integration and customisation of cybersecurity technologies to address sector-specific challenges through our in-house engineering capabilities. This tailored approach ensures that businesses receive solutions that align with their unique requirements and regulatory environments.
NCS’ history of delivering large-scale and complex projects underscores its capability to integrate diverse skill sets across the applications, infrastructure, NEXT, and cybersecurity domains. This holistic approach to cybersecurity, covering multiple layers of the technology stack, positions NCS as a reliable and trusted partner for navigating the challenges of the digital landscape and ensuring comprehensive protection against cybersecurity threats.
References
[WEF22] Earning Digital Trust: Decision-making for Trustworthy Technologies. World Economic Forum, Insight Report, November 2022.
[WDKW22] J. Watts, J. D'Hoinne, D. Koeppen, and C. Winckless. Predicts 2023: Zero Trust Moves Past Marketing Hype Into Reality. Gartner, 6 December 2022.
[WML23] J. Watts, N. MacDonald, and T. Lintemuth. 2023 Strategic Roadmap for Zero Trust Security Program Implementation. Gartner, 13 April 2023.
[WPA23] C. Winckless, P. Proctor, and M. Acosta. Outcome-Driven Metrics You Can Use to Evaluate Cloud Security Controls. Gartner, 28 September 2023.
[CSA21] Cloud Security Alliance (CSA). The Continuous Audit Metrics Catalog, 19 October 2021. https://cloudsecurityalliance.org/artifacts/the-continuous-audit-metrics-catalog/.
[Crace19] J. Crace. The Cambridge Analytica scandal changed the world – but it didn't change Facebook. The Guardian, 18 March 2019. https://www.theguardian.com/technology/2019/mar/17/the-cambridge-analytica-scandal-changed-the-world-but-it-didnt-change-facebook.
[Kom23] M. Komnenic. 109 Biggest Data Breaches, Hacks, and Exposures. Termly, 20 December 2023. https://termly.io/resources/articles/biggest-data-breaches/.
[HWW22] N. Henein, B. Willemsen, and B. Woo. Top trends in privacy driving your business through 2024. Gartner, 5 May 2022.
[WW23] B. Woo and B. Willemsen. Hype Cycle for Privacy 2023. Gartner, 24 July 2023.
[WMH22] B. Willemsen, D. Mahdi, and M. Horvath. Three Critical Use Cases for Privacy-enhancing Computation Techniques. Gartner, 10 November 2022.
[AI-RMF23] NIST AI Risk Management Framework (AI RMF 1.0), January 2024. https://doi.org/10.6028/NIST.AI.100-1.
[SWS22] M. Schneider, J. Watts, and P. Shoard. Innovation Insight for Attack Surface Management. Gartner, 24 March 2022.
[DSS22] J. D'Hoinne, P. Shoard, and M. Schneider. Implement a Continuous Threat Exposure Management (CTEM) Program. Gartner, 21 July 2022.
[FS-ISAC23] Future state technical paper. Post-quantum cryptography working group, FS-ISAC, 2023.