Published: Jan 17, 2025
Zero trust strategies: Effective cybersecurity implementation
Executive summary
Because of its intrinsic benefits, zero trust is gaining prominence among organisations that seek to fortify their cybersecurity defences. Implementing zero trust enhances an organisation’s overall cybersecurity posture by fostering a resilient infrastructure and cultivating an adaptive work environment. At the heart of a zero trust architecture are dynamic policy decisions and enforcement mechanisms that are contingent on the identity of devices or users. This focus, and the adaptability it enables, allows the system to tailor the level of trust based on contextual factors and reduce the vulnerabilities commonly associated with static security measures.
While organisations recognise the advantages of zero trust, there are internal and external challenges that demand attention. Internally, issues such as defining policies at scale, integrating zero trust into legacy and cyber-physical systems, and acquiring organisational implementation and management skills, pose hurdles. Externally, challenges include the ambiguity caused by the unrealistic claims made by vendors in their marketing of zero trust solutions, and the varying levels of maturity of products labelled as “zero trust”.
This article explains the fundamental principles for zero trust implementation and emphasises the need to address internal and external challenges effectively. It explores the core technologies that are pivotal for enabling zero trust, including access management, analytics for detection and response, security service edge solutions, and macro and micro network segmentation. Furthermore, the article provides insight into the zero trust maturity model defined by the U.S. Cybersecurity & Infrastructure Security Agency (CISA). This model outlines a progressive journey to zero trust implementation across five pillars: identity, devices, networks, applications and workloads, and data. Each stage in the maturity model represents a level of advancement to guide organisations from traditional security approaches to optimal zero trust implementation.
The progress toward zero trust is fuelled by its transformative ability to provide a proactive and adaptive security environment. As organisations navigate the implementation journey, understanding the principles, leveraging core technologies, and aligning with the maturity model can help to maximise the benefits of zero trust and fortify defences against evolving cyber threats.
What is zero trust?
Interest in zero trust security has been largely driven by government mandates, vendor hype, ransomware attacks, and the needs of increasingly hybrid workforces. According to Gartner, more than 60% of organisations will embrace zero trust as a starting place for security by 2025[WDKW22].
Zero trust is a transformative security model that challenges the traditional notion of implicit trust within IT architectures. It introduces explicit trusts that are continuously evaluated based on identity and contextual risks. It’s important to note that zero trust is not a standalone security strategy, but rather, a fundamental component within a broader security approach.
In conventional IT environments, security strategies that rely on implicit trust are the norm, and that reliance on implicit trust leads to potential vulnerabilities arising from excessive access. Zero trust addresses these vulnerabilities by replacing implicit trust with a dynamically assessed and explicitly calculated trust model that hinges on identity and context. Establishing a robust identity foundation is imperative for the effective implementation of zero trust.
Zero trust is not confined to networking alone, as its principles can be extended to multiple facets of enterprise system security. Overall, zero trust represents a paradigm shift, as organisations are forced to continuously reassess and adapt their security postures in the face of evolving threats and changing contexts.
The U.S. Department of Commerce’s National Institute of Standards and Technology (NIST) defines zero trust architecture (ZTA) as an approach to cybersecurity that is centred around the principle of “never trust, always verify”. In a zero trust architecture, trust is never assumed for any user, device, or system, even if located within a corporate network. Instead, continuous verification is required of everyone/everything trying to access resources in the network, regardless of its location [RBM20].
Key principles of a zero trust architecture, according to NIST, include:
-
Least privilege access: Users and systems are granted the minimum level of access or permissions needed to perform their tasks. Access is restricted based on the principle of least privilege.
-
Micro-segmentation: Networks are divided into smaller segments and access controls are applied to each segment. This limits lateral movement in case of a security breach.
-
Continuous monitoring: Continuous monitoring of users, devices, and systems is essential. This involves ongoing verification of identity, device health, and other relevant parameters.
-
Risk-based authentication: Authentication mechanisms are adjusted based on risk assessments. For example, additional authentication steps may be required for high-risk activities or for unknown devices.
-
Policy enforcement: Strict access policies are enforced across the network. These policies are often dynamic and can adapt to changes in the IT environment or threat landscape.
-
Encryption: Data is encrypted to protect it from unauthorised access, especially when in transit between users and applications.
A zero trust architecture is designed to address the limitations of traditional perimeter-based security models. It assumes that threats may exist both outside and inside the network and focuses on protecting resources regardless of their locations. This approach aligns with the evolving nature of cybersecurity threats and the need for more robust and adaptive security strategies.
Key benefits of zero trust
Prevailing IT architectures are fraught with implicit trust, a vulnerability that demands elimination to forestall the abuse of unwarranted access. The zero trust model dismantles implicit trust in favour of a model where trust is continuously assessed, explicitly calculated, and dynamically adaptive, contingent on identity and context. This model serves as a guiding principle for security strategies that not only define the architectural landscape but also enhance security posture and fortify cyber-resilience. Organisations embracing the zero trust mindset and architecture stand to gain two pivotal technical outcomes:
-
Resilient infrastructure: Zero trust principles significantly bolster the resiliency of IT infrastructures. A zero trust network, crafted to operate even in the presence of adversaries, excels at containing and managing incidents. This proactive approach diminishes the likelihood of business-impacting events such as ransomware attacks, data compromises, or malware infections. Consequently, this reduction in risk contributes to the overall robustness and security of the business.
-
Adaptive work environment: In anticipation of a more hybrid nature of future work, organisations must provide work environments that are more agile, flexible, and adaptable. A zero trust security strategy seamlessly supports remote workers, using both managed and unmanaged devices, remote data (e.g., IaaS), and remote applications (e.g., SaaS). A secure zero trust implementation will enable the realisation of an "anywhere, any time, on any appropriate device" approach that will be crucial for supporting a dynamic and hybrid workforce.
Implementing zero trust
Key considerations
The implementation of zero trust systems within enterprises requires a systematic and strategic approach. The initial step involves identifying specific use cases that will form the basis of an actionable zero trust strategy. For example, initial use cases might focus on reducing exposure to applications and services, mitigating specific threats by restricting the lateral movement of malware, or isolating software supply chains from attack.
Once the use cases are identified, cybersecurity leaders within the organisation need to establish zero trust strategy and requirements. This process involves a comprehensive assessment of the current environment, with a particular focus on existing identity and access management (IAM) technologies and processes. Understanding the strengths and weaknesses of the current IAM framework is crucial for determining how zero trust principles can be effectively integrated.
The notion of zero trust emphasises fine-grained, just-in-time, access control for user-to-application and application-to-application communications. This approach uses dynamic policy decisions and enforcement mechanisms based on the identity of the device and/or user and can adapt the level of trust according to contextual factors (Figure 1).
While a zero trust architecture (ZTA) promises enhanced security, both internal and external complications pose challenges to its effective implementation. Internally, organisations often grapple with the need to define policies at scale and to manage the rapid pace of policy changes. Legacy systems and cyber-physical systems, such as those for Internet of Things (IoT), Operational Technology (OT), and industrial control systems (ICS), present hurdles to extending ZTA approaches. Additionally, the concurrent deployment of new technologies and processes requires skills that are either hard to acquire or difficult to develop within the existing workforce. Externally, complications are exacerbated by vendor marketing strategies that often dilute the meaning of “zero trust” and create confusion. Products labelled as “zero trust” also tend to come with higher costs compared to legacy alternatives. Moreover, the maturity and integration levels of products supporting a ZTA vary, and that may impact contextual understanding, management, and reporting.
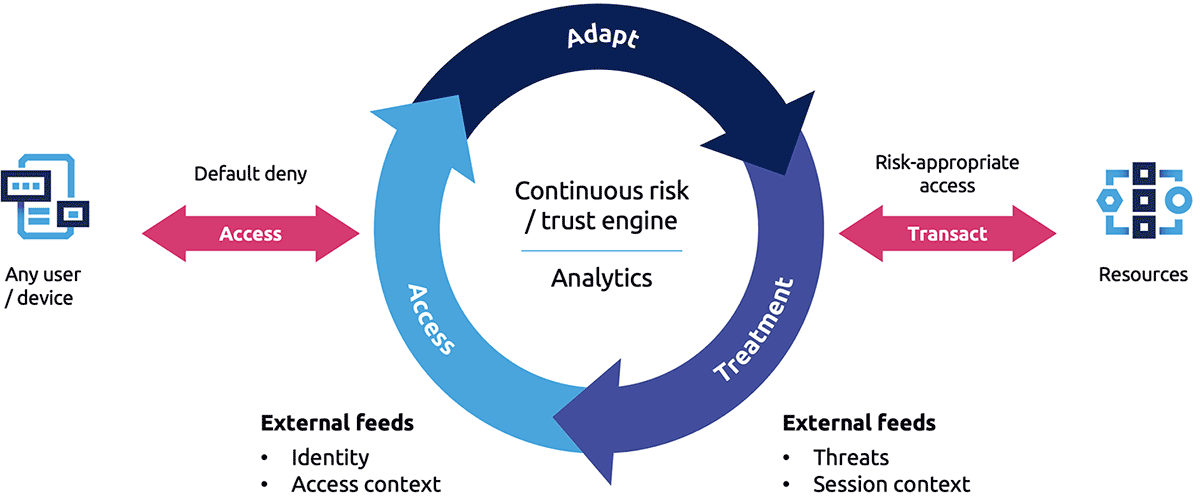
Figure 1: High-level zero trust systems (Source: Gartner 2023 [WML23])
Identifying the optimal projects for ZTA implementation is a complex task due to these challenges. It is crucial to recognise that ZTA is not a one-size-fits-all solution available from a single vendor. Instead, a ZTA involves collaboration among multiple technology providers whose products must seamlessly integrate to establish a continuous-identity and context-aware adaptive trust model.
Internal challenges demand a strategic approach to policy definition and adaptation, especially in the face of evolving technologies and legacy systems. Overcoming skills shortages requires comprehensive training programmes and strategic workforce planning. For external challenges, organisations must navigate vendor landscapes carefully and critically evaluate products labelled as "zero trust" to ensure that they align with security needs and budget considerations.
Roadmap for implementing zero trust technologies
Implementing ZTA requires that cybersecurity leaders prioritise organisational definitions of zero trust and select technology implementations that align with their envisioned future state. Table 1 provides some examples of potential gaps that will need to be addressed to take an organisation from a current state to a desired future state.
Contrary to common misperceptions, transitioning to a ZTA does not necessitate the complete replacement of existing technologies. Many existing tools can support the shift with appropriate configurations. To facilitate this transition, cybersecurity leaders should adhere to the following fundamental principles [WML23]:
-
Context-driven access rights: User account and/or device context, coupled with the criticality of organisational resources, should dictate access rights. This principle emphasises the importance of understanding the context in which users and devices operate to determine the appropriate level of access to sensitive resources.
-
Continuous runtime assessment: Access rights enforcement should not be a static process. Continuous runtime assessment of user account and/or device context, along with the resources being accessed, is crucial. This dynamic evaluation ensures that access rights evolve in response to changing contexts, enhancing security by adapting to real-time conditions.
-
Secured network communications: Regardless of physical location, all network communications between organisational resources must be secured. This principle emphasises the need for robust encryption and security measures for data in transit to mitigate the risk of unauthorised access or interception.
By adhering to these basic principles, organisations can lay the foundation for a ZTA. This approach involves a strategic reassessment and reconfiguration of existing technologies to align with the core tenets of zero trust, and ultimately, to the creation of a security model that prioritises continuous verification and dynamic access controls.
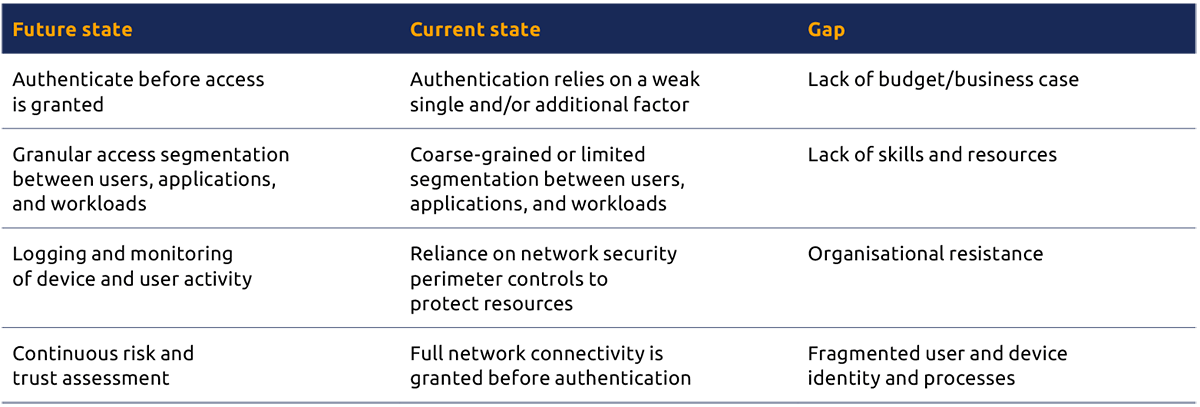
Table 1 : Strategic roadmap for zero trust security programme implementation
It is also important to note that a zero trust strategy must be driven by a business decision that weighs the investment an organisation can/will make versus the benefits that it will accrue from that investment. As organisations improve their capabilities in explaining cybersecurity as a critical business investment, zero trust efforts will be measured against other programme-level security efforts and be viewed as scoped, structured, and proactive as opposed to tactical and reactive.
Core technologies for enabling zero trust
Implementing a ZTA necessitates the integration of diverse technologies from different vendors. According to Gartner, several key technologies form the core of a future-state ZTA:
-
Access management (AM): At the foundation of a zero trust approach, AM involves establishing, enforcing, and managing runtime access controls for internal and external identities across multiple applications. Implementing continuous adaptive AM, password-less authentication, and a security posture with Identity Threat Detection and Response (ITDR) is pivotal in evolving AM practices and shaping zero trust roadmaps.
-
Analytics, detection, and response technologies: In the zero trust evolution of security monitoring and analytics, technologies such as Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), Network Detection and Response (NDR), and Extended Detection and Response (XDR) play crucial roles. These technologies provide security analytics, incident response, and incident response playbook automation, contributing to context-based access controls in a ZTA.
-
Security service edge (SSE): SSE technology secures access to web, cloud services, and private applications irrespective of user or device location. It enhances security and visibility in Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS) environment. SSE, often integrated within a Secure Access Service Edge (SASE) framework, includes Zero Trust Network Access (ZTNA) capabilities. It offers advanced analytics and trust-scoring for identity- and context-based logical access boundaries around private applications and SaaS services.
-
Macro and micro network segmentation: Macro-segmentation refers to traditional grouping based on shared characteristics, such as physical location or business importance, and focuses on controlling north/south traffic within a network. It serves as an in-depth defensive component that complements micro-segmentation. Micro-segmentation involves the creation of granular and dynamic policies with the goal of controlling east/west traffic within a macro-segmentation segment. Implemented at the application layer, it enforces a positive security model and reduces the risks associated with lateral movement.
While these technologies form the core of zero trust, there are additional niche technologies supporting zero trust implementations. A robust ZTA extends beyond core technologies to incorporate a layer-of-defence approach that reduces the attack surface and prevents lateral movement. It is crucial to align these technologies with zero trust principles to create a comprehensive security posture. This layered approach provides a resilient defence against evolving cyber threats and ensures a robust and adaptive security framework.
Journey to maturity
Industry surveys indicate that more than 60% of organisations are either planning or actively implementing a zero trust strategy [OKTA23]. However, Gartner observes that though many clients have a strategy, and are working to implement zero trust technologies, few zero trust implementations can be considered as ‘mature.’ There are several reasons for the nascent state of many ZTA implementations including a lack of interoperability between vendor products, limited scopes of deployment, and a lack of functionality in commercially available products[LLWT23].
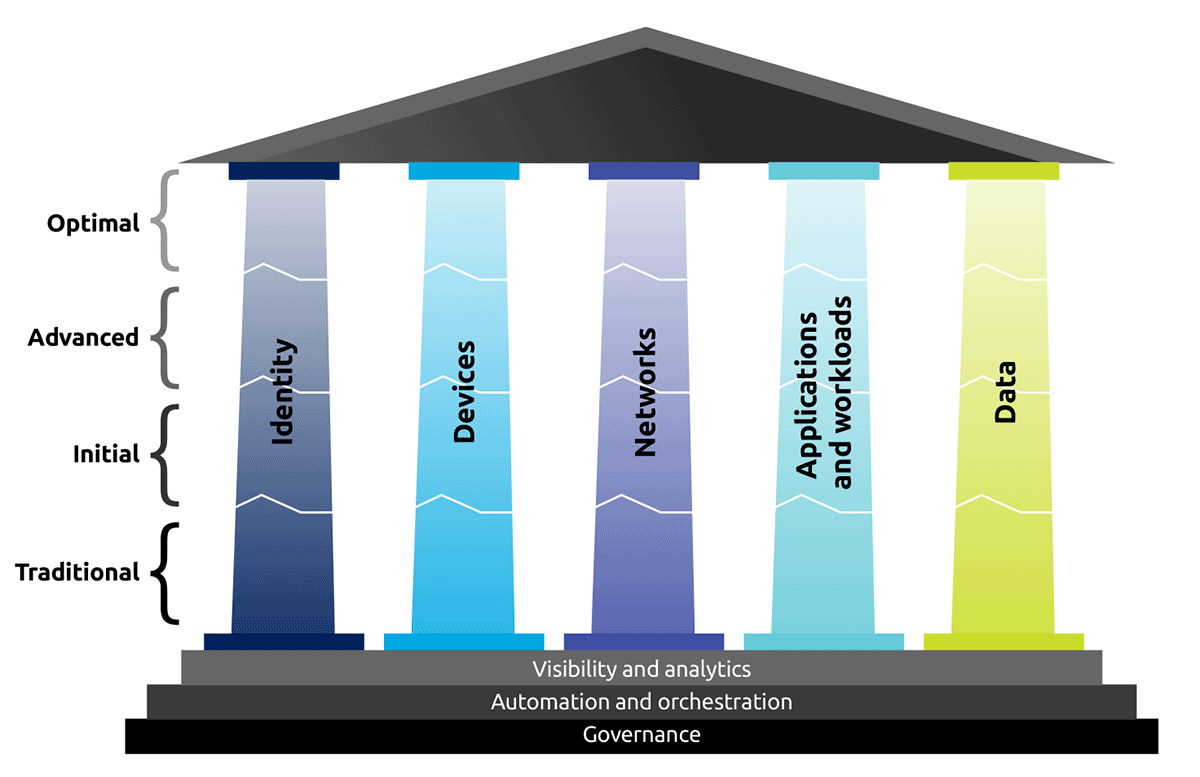
Figure 2: Zero trust maturity evolution as defined by CISA [CISA23]
The journey towards implementing a zero trust architecture (ZTA) involves a gradual process that unfolds over time, reflecting the dynamic nature of cybersecurity challenges. The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has outlined a comprehensive zero trust maturity model that encompasses five pillars: identity, devices, networks, applications and workloads, and data. These pillars are integral to establishing a robust security framework, and each has specific cross-cutting capabilities, including visibility and analytics, automation and orchestration, and governance [CISA23].
As organisations progress through the model, the transition from a traditional approach to an optimal ZTA happens over three distinct stages: Initial, Advanced, and Optimal. This staged approach allows for a systematic evolution that allows organisations to distribute costs over time rather than requiring a substantial upfront investment.
In the traditional stage of the CISA model (Figure 2), organisations rely on manual configurations, static security policies, and siloed enforcement, addressing one pillar at a time. The Initial stage of the CISA ZTA maturity model recommends automation, with attributes being assigned and policies configured dynamically. The adoption of least privilege access at this stage results in responsive changes for post-provisioning and greater visibility increases for internal systems.
At the Advanced stage, organisations implement automated controls for lifecycles and configurations across pillars. Centralised visibility and identity control become the norm and policy enforcement integrates seamlessly. Responses are predefined, and changes to least privilege are based on risk and posture assessments, laying the foundation for enterprise-wide awareness.
The Optimal stage is characterised by fully automated lifecycles and assignments, dynamic policies triggered by automated observations, and just-in-time access, and is the zenith of the ZTA journey. Least privilege access becomes dynamic, ensuring assets and dependencies adhere to enterprise-wide thresholds. Cross-pillar interoperability and continuous monitoring contribute to centralised visibility, offering comprehensive situational awareness.
Organisations navigating this maturity model must evaluate each pillar against specific criteria, at each stage, to ensure consistency across the ZTA framework. By aligning pillar maturity with mission needs and the ability to scale across all pillars, organisations can progressively fortify their security postures. This structured approach empowers organisations to adapt to evolving threats and to ultimately achieve an optimal ZTA that provides dynamic, adaptive, and comprehensive security.
Further details of the zero trust maturity model, including key aspects of the pillar-specific functions for each pillar, and across each maturity stage, can be found here [CISA23].
Zero trust adoption requires cross-organisation collaboration and the involvement of senior leadership, IT personnel, data/system owners, and users. Effective implementation relies on collective engagement to meet design objectives and enhance cybersecurity posture. During ZTA planning, decisions should be guided by factors such as risks, mission, cybersecurity requirements, and operational constraints. The general guide must be tailored based on interactions with external partners, stakeholders, and the service providers involved in ZTA to ensure alignment with organisational dynamics and create a comprehensive approach to security.
How NCS can help you with your zero trust journey
As a leading digital and technology service provider, NCS Cyber has a team of highly qualified and experienced cybersecurity professionals with deep domain expertise in zero trust architectures. This expertise ensures clients receive state-of-the-art guidance tailored to their specific needs, enabling a robust security framework built on the principle of “never trust, always verify.”
Central to our value proposition is a strong specialisation in cryptography through our team of consultants and engineers who are extremely proficient in developing quantum-safe solutions and privacy-enhancing technologies. Our focus on advanced cryptographic measures is fundamental to establishing a secure zero trust environment that protects against both current and emerging cyber threats, particularly those posed by future advancements in quantum computing.
Our competency is bolstered by our partnerships with strategic vendors on a broad spectrum of services ranging from identity and access management to secure network segmentation. These essential components of zero trust architectures ensure strict control and monitoring of access based on verified identities and contextual information, thereby minimising the attack surface, and mitigating potential breaches.
Furthermore, our commitment to continuous support, through consulting and professional services, ensures that the zero trust architecture remains effective and adaptive to new cybersecurity threats and changes within the IT landscape. By offering a comprehensive, flexible, and forward-looking suite of services, NCS empowers clients with readiness for the challenges of the modern digital world through the creation of highly secure and resilient cybersecurity environments.
References
[MMW23] A. McQuaid, N. MacDonald, J. Watts, and R. Kaur. Market Guide for Zero Trust Network Access. Gartner, 14 August 2023.
[RBM20] S. Rose, O. Borchert, S. Mitchell, and S. Connelly. Zero Trust Architecture, NIST Special Publication 800-207, August 2020.
[WML23] J. Watts, N. MacDonald, and T. Lintemuth. 2023 Strategic Roadmap for Zero Trust Security Program Implementation. Gartner, 13 April 2023.
[LLWT23] T. Lintemuth, A. Lerner, J. Watts, and K. Thielemann. Predicts 2024: Zero Trust Journey to Maturity. Gartner, 15 December 2023.
[OKTA23] okta, The State of Zero Trust Security 2023, https://www.okta.com/au/state-of-zero trust/.
[CISA23] Cybersecurity and Infrastructure Security Agency (CISA), Zero Trust Maturity Model, version 2.0, April 2023.