Published: Jan 17, 2025
The last line of defense: Cryptography's role in cybersecurity
Executive summary
Cryptography is foundational and ubiquitous in data security, yet its importance and complexity are often undervalued. As computing technology becomes increasingly powerful and sophisticated, strong cryptography is more crucial than ever. It can serve as the last line of defence in a zero trust model that relies on multi-layer security to protect an organisation’s most valuable assets. However, implementing cryptography correctly is challenging and requires specialised expertise. This article explores the complexities of cryptography and provides insights on managing the cybersecurity risks associated with its use and management. We emphasise the importance of cryptographic visibility—maintaining an up-to-date inventory of all cryptographic assets—and cryptographic agility – the ability to quickly adapt to new threats by updating or replacing algorithms. These practices are essential components of good cyber hygiene that will ensure robust and adaptable cryptographic security. By focusing on these areas, organisations can better protect their data and maintain the integrity of their systems in an ever-evolving threat landscape.
Cryptography translates to trust
Cryptography is the practice of securing information by transforming it into an unreadable format that is only decipherable by those who possess a secret key. In the digital world, cryptography is a cornerstone of trust. It acts as the backbone of secure communication and data protection, enabling trust in online interactions, and safeguarding valuable information. More than 96% of current web traffic is protected through cryptography (Figure 1).
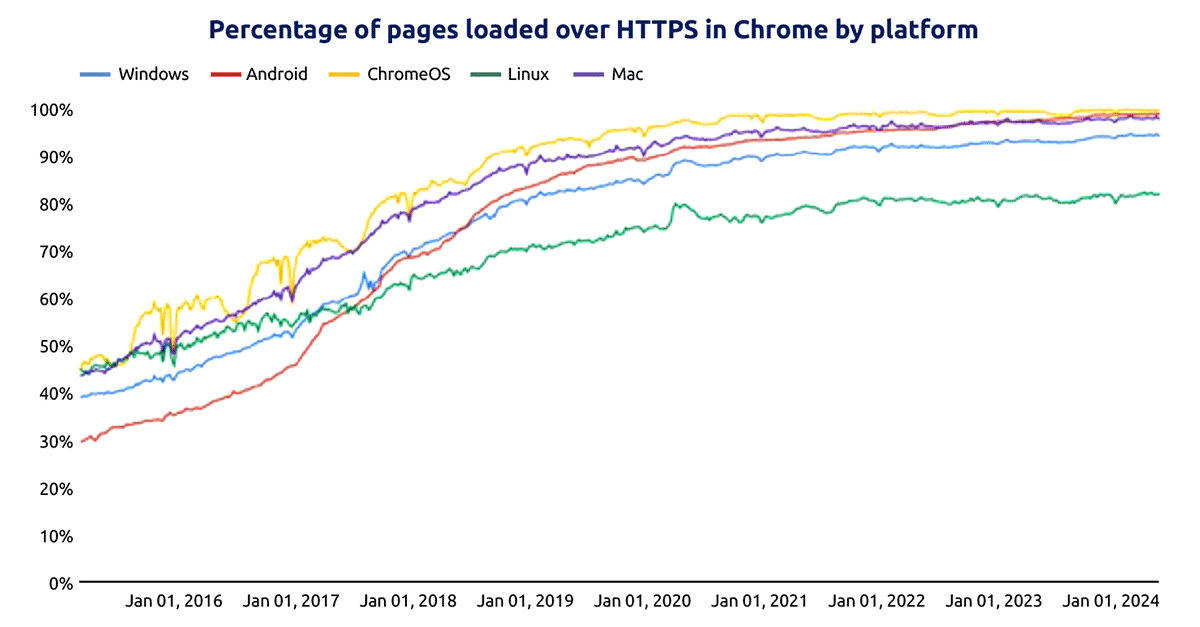
Figure 1: Google transparency report indicated that more than 96% of today’s web traffic is encrypted.
Cryptography is essential to cybersecurity in multiple ways. It ensures confidentiality and protects sensitive data from unauthorised access and enables the detection of tampering or alteration of data for integrity verification. It also serves as an authentication mechanism, through the use of digital certificates, for identity verification of users and systems. Furthermore, cryptographic controls are often required for regulatory compliance, with many regulations mandating the implementation of specific cryptographic measures to safeguard data. By fulfilling these roles, cryptography provides a robust foundation for securing information and maintaining trust in digital communications and transactions.
Emerging trend: zero trust and last line of defence
For defence-in-depth, or multi-layer security, cryptography serves as the last line of defence. If a network or system is compromised, strong cryptography is crucial for preventing access to critical assets. It provides resilience against data breaches, ensuring that even if all other security measures fail, the encrypted data remains protected. Cryptography is fundamental to the zero trust model, supporting authentication, enforcing access control policies, and securing data both at rest and in transit. The encryption of sensitive information ensures that unauthorised parties cannot access or decipher the data, and that confidentiality and integrity can be maintained, even in a compromised environment.
Kevin Kenan, in his book Cryptography in the Database: The Last Line of Defence [Ken05] emphasises the critical role of cryptography in safeguarding databases and positions it as the final layer of defence against potential breaches. As the ‘crown jewels’ of any organisation, databases require an additional layer of protection—strong cryptography—as the ultimate shield for scrambling data into unintelligible ciphertext that becomes useless if accessed by unauthorised parties.
Intricacies of cryptography
Effectively implementing cryptography is challenging for a number of reasons:
- Algorithmic complexity: Cryptographic algorithms are based on complex mathematical concepts such as prime numbers, finite fields, and elliptic curves that require specialised knowledge to understand and apply correctly. A subtle design flaw can significantly weaken an algorithm. For example, a flaw might compromise the required level of randomness or unintentionally reveal partial information about the secret key used for encryption.
- Implementation challenges: Turning theoretical cryptographic algorithms into practical applications introduces complexity. Issues can arise from programming errors, side-channel information leaks, and the use of insecure random number generators. These implementation flaws can undermine the security of the cryptographic system, making it vulnerable to attacks.
- Key management: Effective key management is critical for cryptographic security but is notoriously difficult. Setting up and maintaining a Public Key Infrastructure (PKI) is complex, particularly establishing a reliable root of trust rather than using self-signed certificates. Additionally, some organisations fail to update or renew cryptographic keys in their critical systems, further compromising security.
- Human factors: Humans are often the weakest link in cryptographic security. We are prone to errors and may overlook or simplify complex aspects of cryptography. Mistakes in key management, configuration errors, and the improper handling of cryptographic materials are common issues, introduced by humans, that can lead to vulnerabilities.
Given these challenges, getting cryptography right is a not-trivial matter, and managing cryptographic risks is critical.
Cryptographic risks
The improper use and management of cryptography can lead to increased risks of compromising data security or cybersecurity incidents. Such cryptographic risks can emerge from several sources:
- Legacy applications often use weak cryptographic methods that are challenging to upgrade. These outdated systems can create vulnerabilities that are difficult to address without extensive modifications.
- Vendors bound by existing support contracts may struggle to promptly implement new cryptographic algorithms in response to common vulnerabilities and exposures (CVE) reports. This lag in updating can leave systems exposed to known vulnerabilities for extended periods.
- New discoveries and breakthroughs in cryptographic research can render existing algorithms insecure. As researchers uncover weaknesses, or develop more advanced cryptographic techniques, previously secure methods may become vulnerable.
An evolving landscape requires constant vigilance and adaptation to maintain robust cryptographic defence. Ongoing updates and revisions to cryptographic practices and systems are essential as the dynamic nature of cryptography means that what is considered secure today may not be secure tomorrow.
Lessons learned from past decades
Let us take the Transport Layer Protocol (TLS) protocol, today’s most widely used cryptographic protocol, as an example. Figure 2 summarises the evolution of the TLS protocol.
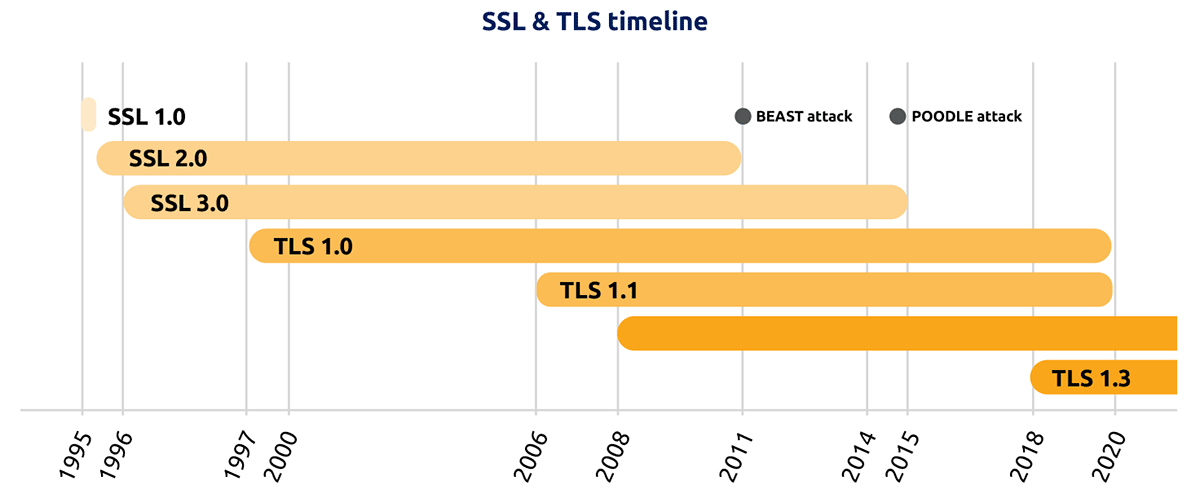
Figure 2: Evolution of the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols, which have been the foundation of securing web traffic.
When TLS was first introduced, then called Secure Sockets Layer (SSL), it had numerous design flaws and vulnerabilities. SSL 2.0, for example, lacked message integrity protection and relied on weak cryptographic algorithms like RC4 and SSL 3.0, and was susceptible to the POODLE attack, which exploited a fallback mechanism to downgrade secure connections to vulnerable sessions.
To address these issues, stronger cryptographic algorithms were incorporated into TLS 1.2, released in 2008. This version was widely adopted and remained a standard for a considerable period. The most recent version, TLS 1.3, brought significant improvements that focus on both performance and security. TLS 1.3 simplified the handshake process and eliminated outdated cryptographic algorithms, representing a major overhaul.
Some key lessons from the development of TLS over the past two decades include:
- Continuous evolution: Security protocols like TLS must continuously evolve to counteract emerging threats and vulnerabilities. The progression from SSL to TLS 1.3 demonstrates the necessity of ongoing updates and enhancements to maintain robust security.
- Backward compatibility risks: Supporting outdated protocols and algorithms for compatibility purposes can introduce significant vulnerabilities. It is crucial to phase out weak cryptographic algorithms to protect against potential exploits. The transition away from SSL to newer versions of TLS highlights the importance of updating cryptographic standards.
- Implementation matters: Even the most secure protocols can be compromised by poor implementations. A prime example of this is the “Heartbleed” vulnerability in the OpenSSL software library, which exposed significant weaknesses despite the underlying protocol’s strength. This underscores the importance of meticulous implementation and regular audits to ensure security.
- Balancing performance and security: Achieving the best security and performance simultaneously is challenging. TLS 1.3 demonstrates the importance of achieving a balance between these two aspects. The latest version of TLS not only enhances security but also optimises performance by streamlining the handshake process and removing obsolete algorithms.
Recommended cyber hygiene
At NCS, we have qualified and competent cyber professionals who can assist clients in managing their cryptographic risks. Our assessment methodology aligns with established frameworks such as the NIST Cybersecurity Framework [CSF24] as well as cybersecurity guidelines provided by local agencies. Central to our approach are two key practices: cryptographic visibility and agility. Cryptographic visibility involves maintaining a comprehensive inventory of cryptographic assets to ensure that all encryption methods and keys are accounted for and monitored. Cryptographic agility ensures quick adaptation to new threats through the updating or replacement of algorithms as required. Together, these practices form a robust strategy to effectively manage and mitigate cryptographic risks.
Cryptographic visibility
Having good visibility of what cryptography systems are in place and where and how cryptography is used within an organisation is essential for effective cryptographic risk management. This visibility allows for a comprehensive inventory of cryptographic tools and protocols and ensures that no critical assets are overlooked. It helps organisations to prioritise risks based on the sensitivity and importance of the data and allows for efficient resource allocation to the most critical areas.
As illustrated in Figure 3, cryptography plays a crucial role in telco customer-facing use cases by ensuring secure communication and protecting personal data. TLS encrypts online interactions between customers and telco servers, safeguarding sensitive information such as login credentials and personal data. Telco-provided VPNs enhance security by encrypting all internet traffic from a customer’s device, especially over public Wi-Fi networks. Furthermore, encryption protects customers from the data stored in telco databases and ensures that it remains inaccessible without decryption keys. End-to-end encryption for SMS and voice services ensures that only intended recipients can access the content of messages and calls.
Internally within a telecom operator, cryptography secures the communication links and operational data within its networks. Encryption protects links between base stations and core network gateways, preventing unauthorised access to data such as call metadata and user locations. Encrypted channels safeguard sensitive operational data, such as configuration updates sent to base stations, from interception and manipulation. In the SIM provisioning process, cryptographic keys embedded during manufacturing authenticate and encrypt communications to prevent cloning and fraud. Encrypted data exchanges during SIM distribution secure provisioning information from interception or alteration. Overall, cryptography ensures secure communication, data protection, and operational integrity in the provision of telco services.
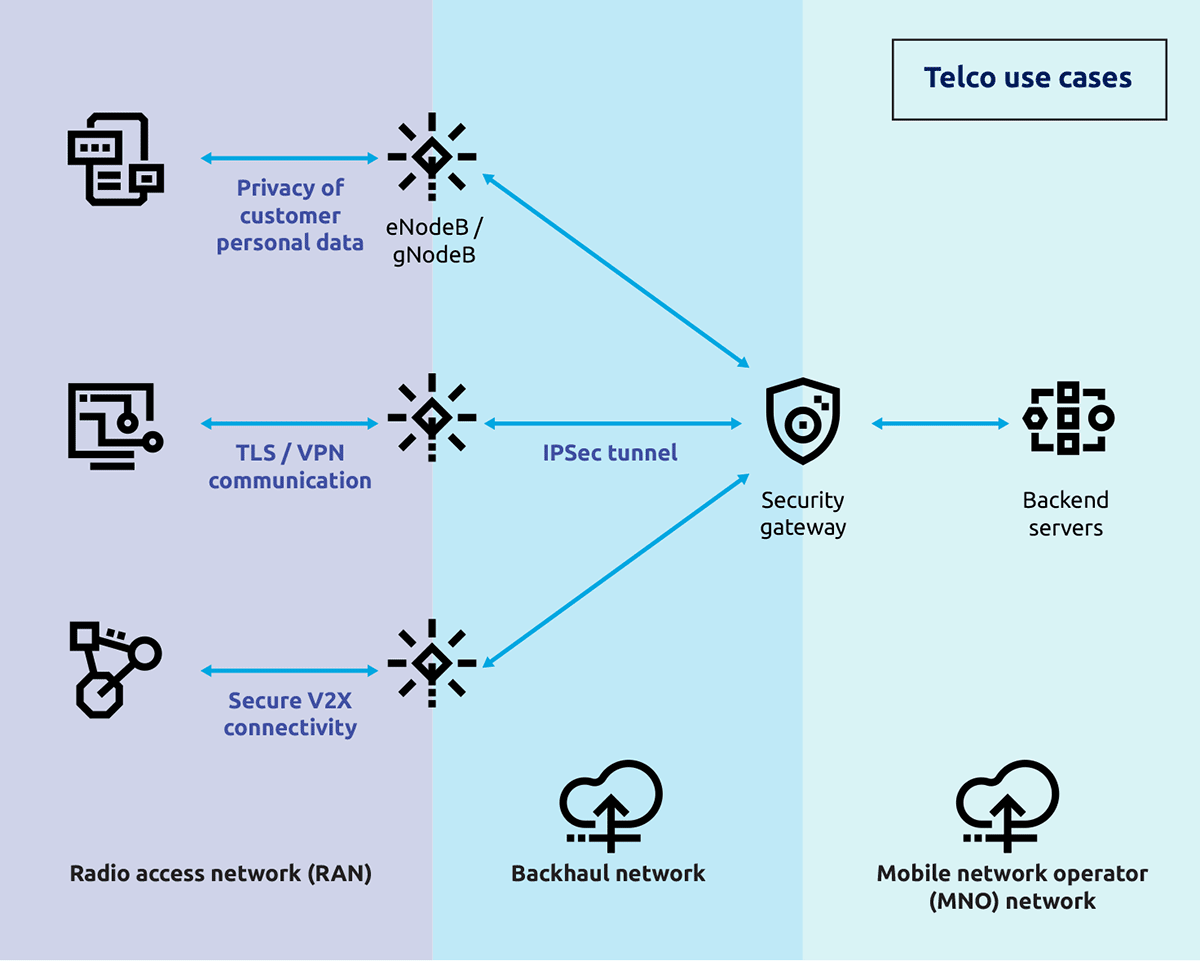
Figure 3: Examples of usage of cryptography in telco use cases
A number of tools, both code-based and network-based, can be used to build a comprehensive cryptographic inventory, which is essential for effective risk assessment. This inventory should encompass information associated with all cryptographic assets deployed within or owned by the organisation. These assets may be related to in-house or third-party applications, and internal or external network services. Furthermore, the inventory should specify the lifetime of data that needs to be protected, and the implication to business goals if the data is compromised. By thoroughly cataloguing these elements, organisations can better identify vulnerabilities, prioritise mitigation efforts, and ensure that robust security measures are in place to protect sensitive information and maintain operational integrity.
Cryptographic agility
Once we have good cryptographic visibility, it is crucial to implement processes and mechanisms that can be used to swiftly respond to new cryptographic threats, while minimising the impact on interoperability with existing systems. This will ensure that as new vulnerabilities or advancements in cryptographic techniques arise, the organisation can adapt quickly without compromising security or disrupting operations. Establishing such responsive processes will involve regular monitoring, updating cryptographic protocols, and maintaining flexibility in systems design to integrate new algorithms seamlessly. This proactive approach will help in maintaining a robust security posture against emerging threats.
Cryptographic agility is a key concept in this adaptive approach. Cybersecurity products designed with cryptographic agility can access multiple cryptographic algorithms, allowing system owners to configure the product to use the most suitable algorithms for their specific needs. When existing configuration options are no longer sufficient, these systems have built-in processes to introduce new configuration options that ensure continuous protection. This means that as older algorithms become obsolete or new, more secure, algorithms are developed, the system can be updated with minimal disruption. By incorporating cryptographic agility, organisations can stay ahead of threats and be confident that their security measures evolve in line with technological advancements and emerging vulnerabilities.
Figure 4 shows how a crypto-agile TLS protocol can be configured to adapt swiftly to new threats. Suppose an application within an organisation relies on TLS 1.3, which supports cryptographic algorithms X and Y. If a vulnerability is discovered in algorithm X, rendering TLS 1.3 insecure, the system owner can quickly check the cryptographic inventory to see if the affected algorithm is in use. If it is, there should be a process to promptly disable algorithm X. Consequently, when a new request for a secure connection is made, the system will reject the vulnerable algorithm and instead opt for the secure alternative, algorithm Y. This will ensure continued security without significant disruption to daily operations.
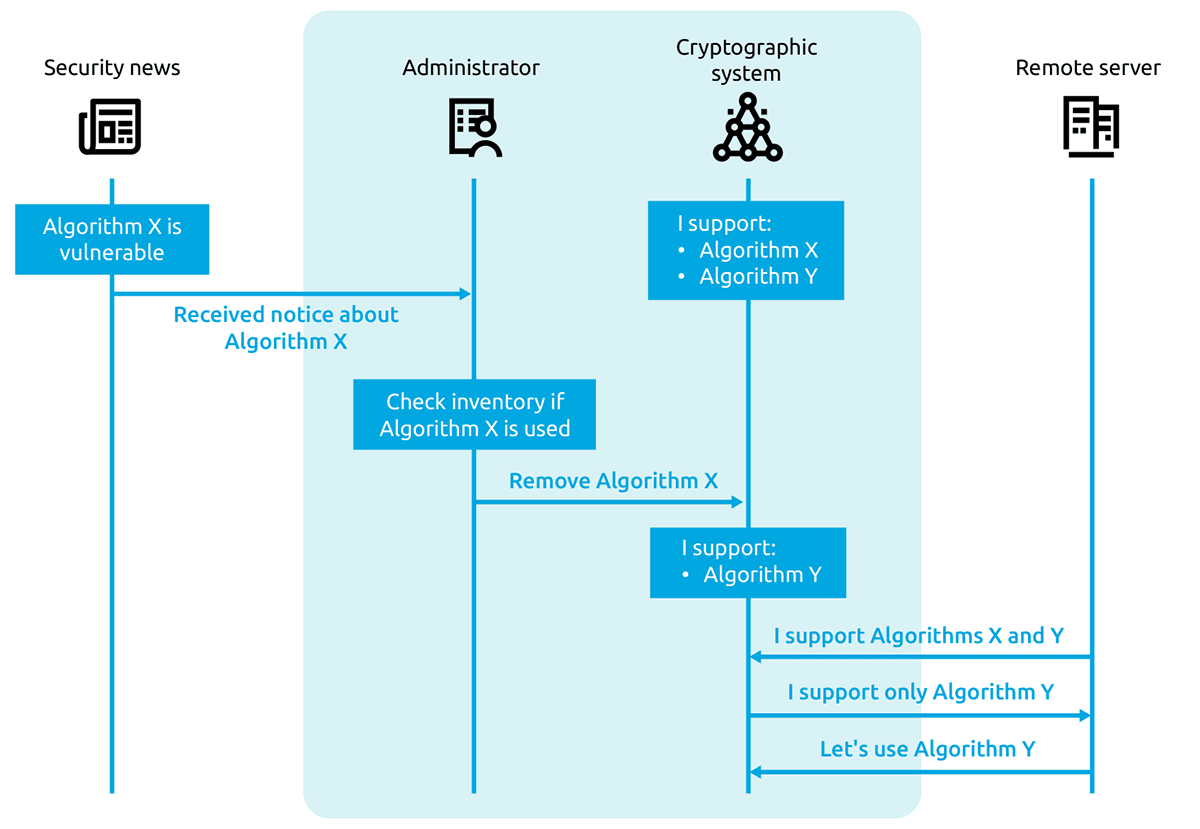
Figure 4: In the event there is a new cryptographic threat or vulnerability, update cryptography without impact to the overall system. (Source: Guidance on becoming cryptographically agile - ITSAP.40.018, May 2022.)
In summary, crypto agility is a crucial DevSecOps activity that involves several key components. First, it requires maintaining an up-to-date inventory of all cryptographic algorithms currently in use to ensure a clear understanding of the organisation’s cryptographic landscape. Second, it involves writing and enforcing crypto replacement policies that define procedures for updating or replacing algorithms when vulnerabilities are discovered or when new, more secure, options become available. Third, a requirement for testing and validating these implementations is essential to ensure that changes do not introduce new vulnerabilities or disrupt existing systems. Finally, continuous monitoring of changes to applications, networks, and data is necessary to detect and respond to potential threats promptly. By integrating these activities, organisations can ensure a robust and adaptable cryptographic security environment that is capable of responding swiftly to emerging threats to fortify their last line of defence.
References
[Ken05] K. Kenan. Cryptography in the Database: The Last Line of Defence. Addison Wesley, 2005.
[CSF24] The NIST Cybersecurity Framework (CSF) 2.0, Feb 2024. https://doi.org/10.6028/NIST.CSWP.29