Published: Jan 17, 2025
Engineering cyber resilient operational technology systems
For large complex systems, there are literally millions of ways to fail to meet objectives, even after we have defined the “right system”. It is crucial to work all the details completely and consistently and ensure that the design and technical activities of all the people and organisations remain coordinated.
The Art and Science of Systems Engineering, NASA
Introduction
For complex engineering projects, adopting a systematic security engineering process is a vital step in developing Cyber Resilient Systems1. Not only is it commonly mandated for compliance reasons, but it is also the key enabler for:
- Integrating all activities related to achieving a well-planned and secure system into meaningful outcomes that meet security objectives
- Prioritising high value security controls
- Making meaningful trade-offs2
- Ensuring traceability and clear communication of impact, and
- Disseminating information to other stakeholders and downstream activities
However, in many projects, the project teams struggle, often encountering pitfalls that lead to:
- Inefficient and ineffective use of the time and efforts of stakeholders in security-related workstreams
- Security requirements that do not align with other considerations
- Communication gaps that impact the dissemination of information to stakeholders or downstream activities
- Challenges in conducting assessments and providing well-supported justifications for deviations and requests3
- Reworking cycles to remedy these issues
Collectively, this can result in significant costs due to wastage. Many of these pitfalls can be avoided by working with an experienced Operational Technology (OT) Security team that can skillfully lead and help stakeholders navigate the complexities. This paper highlights the six important areas for OT Security teams supporting complex engineering projects to consider, with examples drawn from the real-life delivery of a project that involved fabricating a new substation for an offshore wind farm.
Understand process best practices
We cannot overemphasise the importance of having a systematic process and a clear understanding of its requirements. This involves not only a thorough grasp of cybersecurity activities, but also the crucial integration of these activities and considerations into the overarching systems engineering and project processes.
In the context of critical systems or systems delivery in highly regulated industries, it is typically mandatory to establish a security programme that incorporates lifecycle process best practices. Applicable highly regulated industries include Aviation, Maritime, Land Transport & Rail, Healthcare, Power & Utilities, Oil & Gas, and Critical Information Infrastructure.
Various publications discuss compliance requirements or provide guidance on security programmes and best practices4. While general concepts and best practices are usually consistent across these publications, the level of detail on specific subtopics may differ. In our experience, PD CLC/TS 50701, the cybersecurity standard for rail applications, provides the clearest guidance on executing a robust security programme. Although it is intended for rail systems, it is aligned with ISA/IEC 62443, making it relevant and applicable across various industries. The process described in PD CLC/TS 50701 is also largely consistent with the process our team applies for our consultancy projects.
The PD CLC/TS 50701 standard provides detailed elaboration on the cybersecurity activities and the integration of cybersecurity with other project activities and deliverables across the 13 lifecycle phases (0-12), aligned with EN50126 Railway Applications – The Specification and Demonstration of Reliability, Availability, Maintainability and Safety (RAMS). Table 1 shows details extracted from PD CLC/TS 50701 as a subset of these lifecycle phases for illustration5 purposes. We recommend reading the relevant chapters of the original publication for complete details. Appendix B: ‘Example Process Flowchart for Security and Safety Co-engineering’ further illustrates the process for security and safety co-engineering.
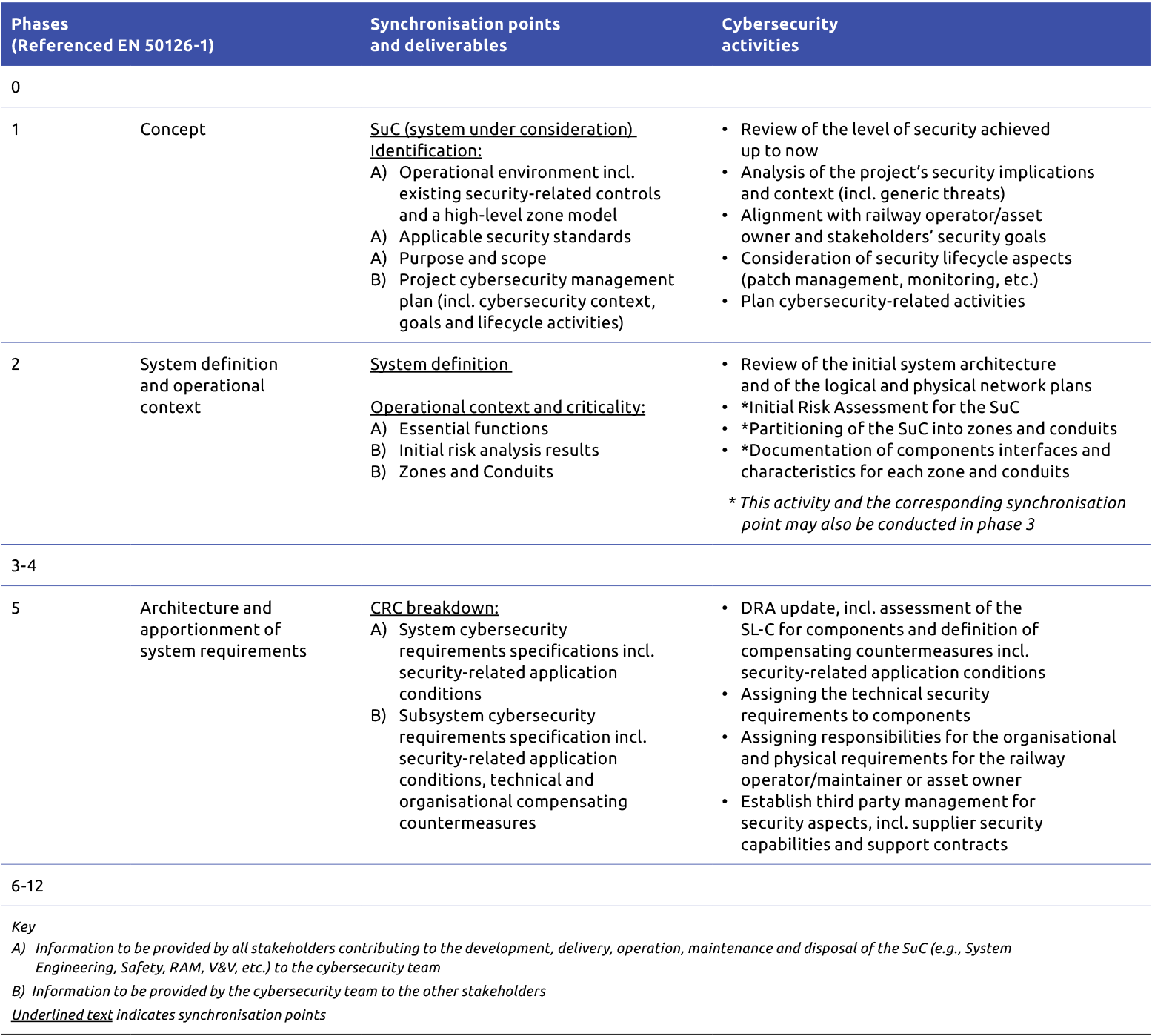
Table 1: Redacted contents on security-related activities within a railway application lifecycle (Reference: PD CLC/TS 50701:2023)
Determine the high-level compliance requirements and applicable publications
At the beginning of an advanced system engineering project, the OT Security team may face confusion about how to approach the project. Team members may be aware of some compliance standards, such as IEC 62443, ISO 21434, CLC/TS 50701, or DO-326, and specific functional requirements like central logging, continuous monitoring, and equipment patching. Additionally, the project may require various documentation deliverables, such as an OT Security management plan, vendor management plan, account management policy, and vulnerability management procedure.
However, the initial list of standards provided may not cover the full scope of necessary compliance. For instance, Singapore regulations mandate that Critical Information Infrastructure (CII) systems comply with CCOP, healthcare systems handling patient data may be subject to HIPAA, and airborne systems requiring airworthiness certification may need to adhere to standards like DO-178. Therefore, relying solely on the standards guidance provided by project stakeholders may result in incomplete adherence to the complete regulatory and standards requirements.
Meeting functional requirements such as central logging impacts the entire system development lifecycle. This necessitates prioritising devices with logging capabilities and built-in log exportation features, which must be validated throughout the development process. To ensure that these activities are properly executed, adopting a suitable framework such as the approach described in NIST SP 800-160 is essential. Additionally, other guidelines and publications may be needed to develop specific documentation deliverables such as an account management policy.
The OT Security team should proactively conduct its own research and assessments to determine the full suite of applicable regulations, standards, and publications. Early discussions with project stakeholders are crucial to ensure that all requirements are identified and understood. Documenting this information in relevant management plans, such as the OT Security management plan and vendor management plan, is essential for effective information flow and alignment throughout the project.
Understand the context for systems and stakeholders
Understanding the contexts—for stakeholders, systems, and roles—is crucial for successful planning and project execution in an advanced systems engineering project. This comprehensive understanding lays the foundation for effective planning and ensures that all aspects of the project are well-coordinated and aligned with the goals.
The system context, including early indicators from risk assessments, is vital for planning and assessing the system's criticality. Before conducting detailed risk assessments, initial judgments can be made based on the system's intended function, asset composition, interactions with other systems, communication interfaces, and the data traversing these interfaces. These early insights help in shaping the security strategy and expected efforts for the system.
In such projects, the OT Security team will likely interface with multiple stakeholders, including regulators, asset owners, and system operators. For systems in highly regulated domains, or requiring external certifications, stakeholders may also include regulators or external compliance/certification bodies. Security and the Information Security Management System (ISMS) considerations impact most stakeholders. Planning and strategy activities that lead to deliverables like plans and procedures require an understanding of these stakeholders' contexts to define their roles and responsibilities within the ISMS framework effectively.
As the subject matter experts, the OT Security team is expected to provide advice to other stakeholders on project efforts, activities, and various scenarios. Its expertise is crucial for guiding stakeholders through the planning process, helping them understand the projected efforts and activities affecting their work streams, and advising on the next steps for different scenarios, such as seeking deviations or waivers and determining endorsements. A deep understanding of the context is essential for performing this advisory role professionally.
Understand the expected information available, shortlist the applicable non-cybersecurity technical deliverables for tracking, and determine the information gaps
Security-related activities and deliverables cannot be accomplished without close participation and input from technical subject experts and project sub-teams. Security practitioners must be able to play an active role to lead the process, as they cannot rely on non-security-trained stakeholders to know or anticipate the required information or to document it in a format directly relevant to security activities. Effective and meaningful discussions and clarifications are often necessary to bridge this gap.
Security practitioners should leverage non-security resources to gain the initial context needed to lead meaningful discussions, assessments, and surveys. In our experience, the master document list (or master document register) of the project is an excellent starting point. It provides insights into the information that will be documented throughout the project lifecycle, and when this information will become available.
Wiring construction diagrams or electrical connection diagrams are valuable references for understanding the expected network and communication interfaces between components. We have used information from these documents to create system network diagrams and data flow diagrams for threat modelling. Additionally, documents on functional safety assessments and failure analysis are useful for understanding the functional criticality of system components and the corresponding impact of failures. These documents provide meaningful knowledge that is essential for performing cybersecurity risk assessments.
Implement adequate security controls
Implementing security controls involves the act of balancing the adequacy of protection for the system against the cost of implementing those security controls. A risk-based approach towards implementation will allow adequate security controls while also ensuring the distribution of budget across the system based on needs and necessity.
In our experience, IEC 62443-3-3 is a great reference that provides a comprehensive list of security controls to be considered, and a breakdown of controls based on the severity level of the system components. When planning the security controls to implement, planners can reference the publication as a good starting point, even for projects that do not mandate IEC 62443 compliance.
In summary
Engineering cyber resilient OT systems requires meticulous planning, a thorough understanding of the system and stakeholder contexts, and effective collaboration among various teams. The OT Security team plays a pivotal role in guiding stakeholders and ensuring that security requirements are well-integrated into a project’s broader objectives. They undertake six main tasks: understanding compliance requirements, engaging stakeholders, conducting risk assessments, implementing security controls, ensuring continuous monitoring, and facilitating patch management. By leveraging non-security resources and integrating early risk assessment indicators, the team can develop a comprehensive security strategy that aligns with a project’s goals and lifecycle. This proactive and context-driven approach enhances the security posture, facilitates efficient resource use, and ensures that security considerations are seamlessly incorporated into the system development process.
Appendix A: Detailed Extracts from PD CLC/TS 50701:2023 on Cybersecurity Process and Synchronisation
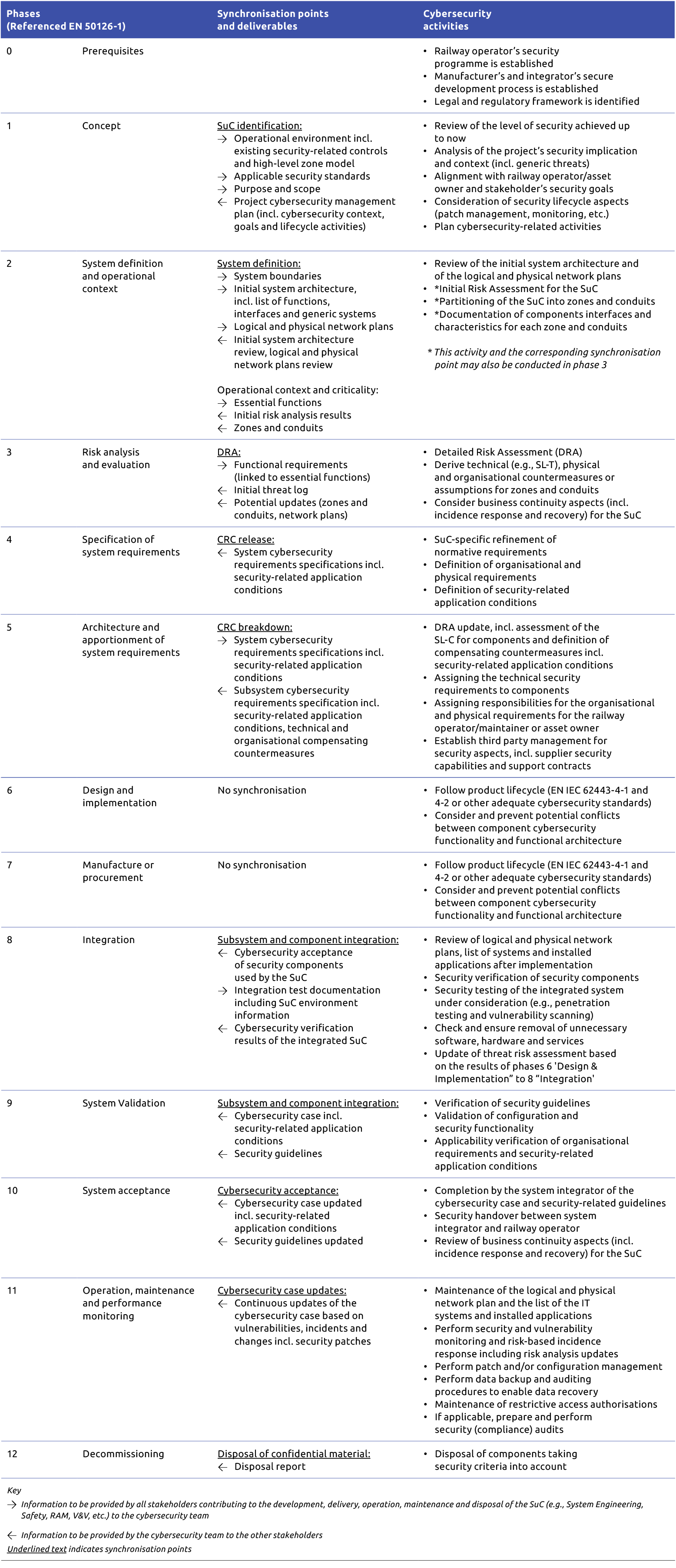
Table 2: Security-related activities within a railway application lifecycle (Source: PD CLC/TS 50701:2023)
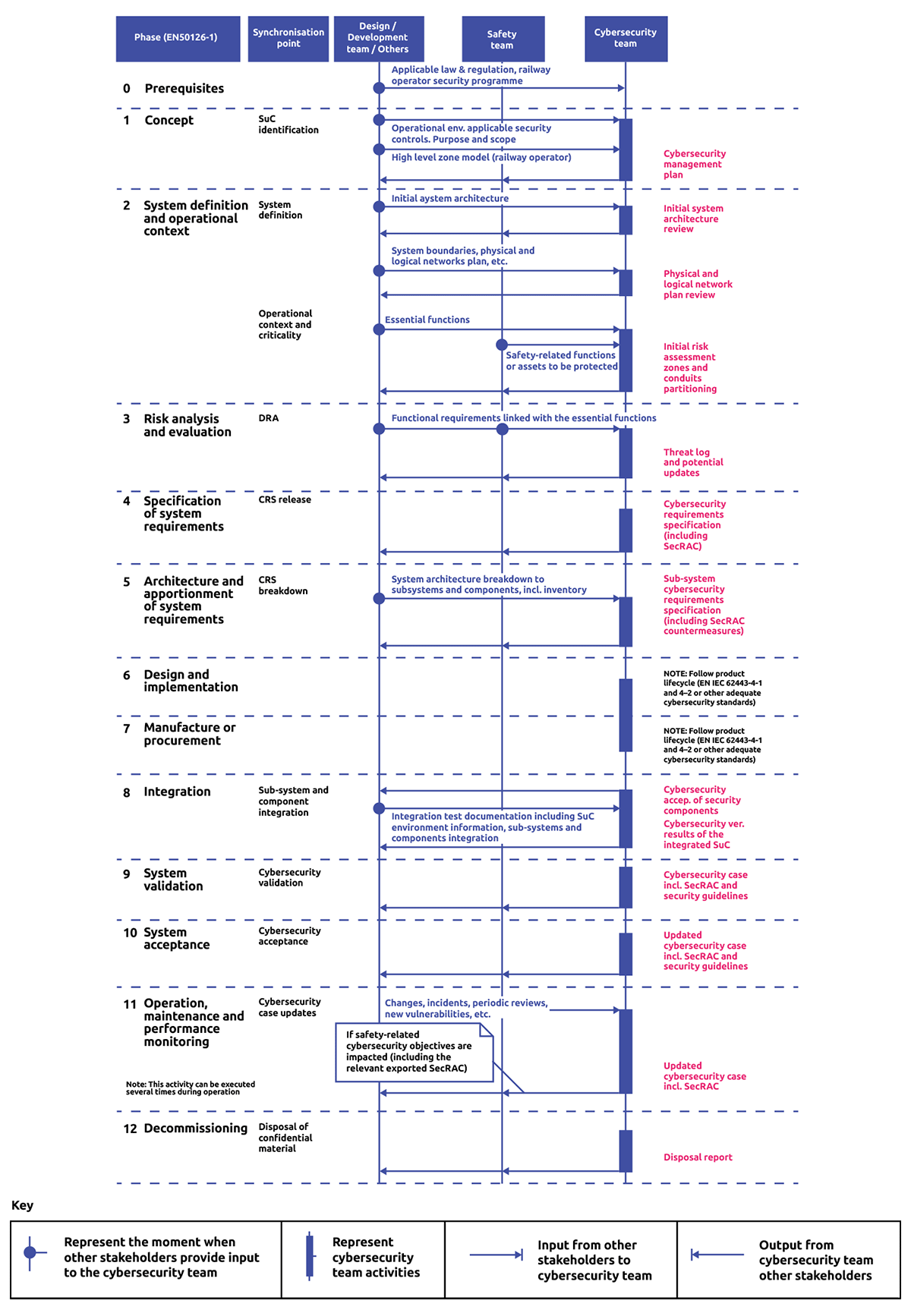
Figure 1: Synchronisation between cybersecurity team and other stakeholders (Source: PD CLC/TS 50701:2023)
Appendix B: Example Process Flowchart for Security and Safety Co-engineering
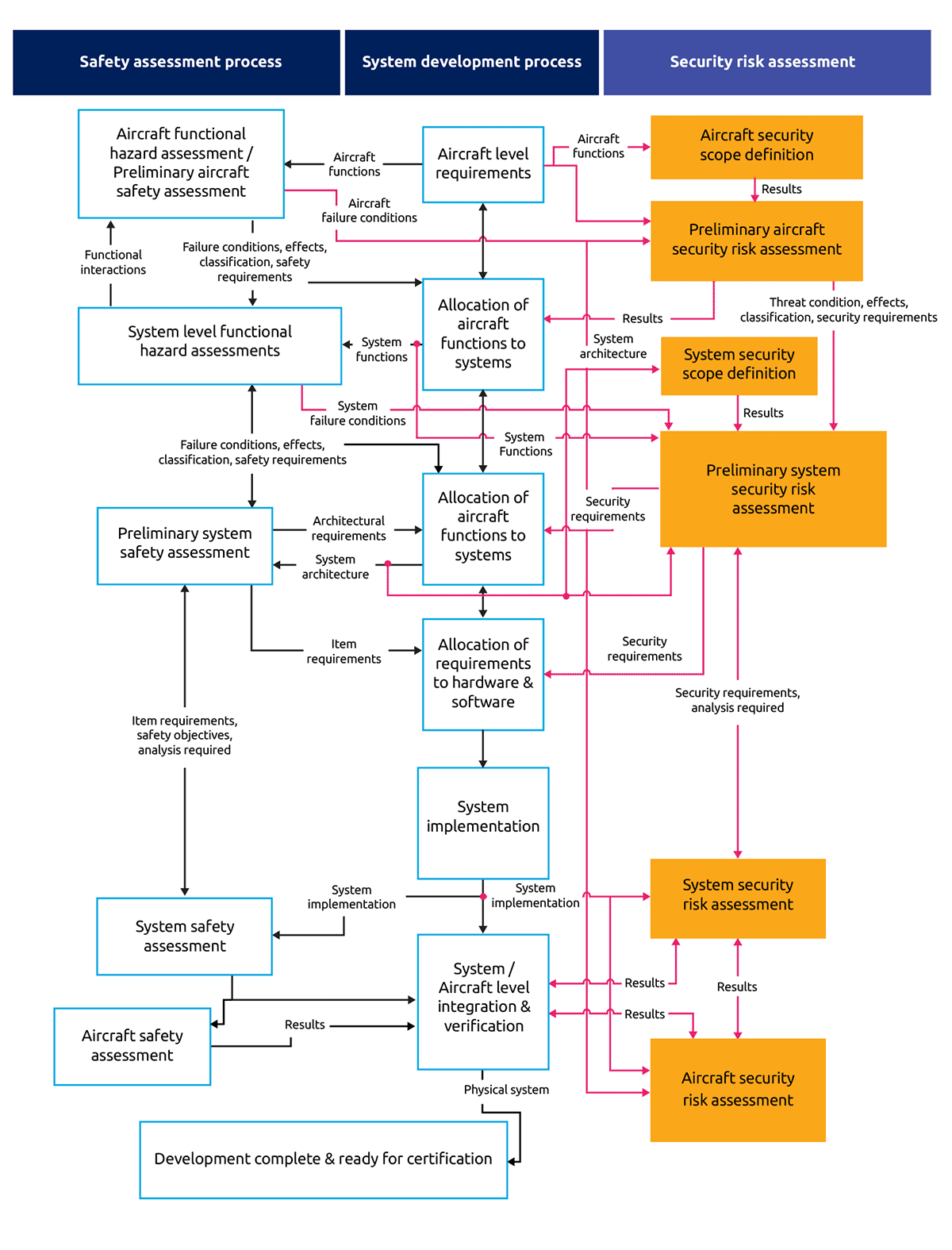
Figure 2: Airworthiness security process as part of Aircraft Certification Process (Source: Recommendations for Security and Safety Co-engineering, Information Technology for European Advancement)