Published: Oct 17, 2025
Quantum-safe cryptography: When and how to start
Quantum computing is racing ahead. What once felt like science fiction is now edging into reality and that spells big change for how we secure data. The encryption standards we all rely on today may not stand up tomorrow.
In this article, you’ll learn why post-quantum cryptography (PQC) matters now, what risks it poses for organisations, and the practical steps you can take to prepare. We’ll walk you through a roadmap that makes PQC migration achievable, explain the business case for acting early, and highlight how NCS can help you build confidence in a quantum-safe future.
Key takeaways
- PQC migration is a business necessity, not just an IT project
Quantum disruption won’t just affect encryption algorithms, it could undermine customer trust, compliance, and business continuity. Migration must be a board-level priority. - Start discovery and inventory work now to avoid bottlenecks later
Most organisations don’t know where their cryptographic assets are. Beginning discovery early makes the entire migration process faster, cheaper, and less disruptive. - A phased roadmap lowers risk and disruption
PQC migration is complex, but it doesn’t have to be chaotic. Breaking it into clear phases, from assessment through governance, allows businesses to move steadily and securely. - Early movers win customer trust and regulatory confidence
Acting ahead of “Q-day” means more than compliance. It positions organisations as forward-thinking, resilient, and prepared, all qualities customers and regulators value.
Why quantum matters now
Quantum computing is no longer just a research milestone. Breakthroughs are happening at pace, with governments and enterprises investing heavily in quantum research and applications. While the business potential is exciting, the security risk is equally urgent: most of today’s digital infrastructure, from online banking to cloud storage, depends on cryptographic algorithms that quantum machines will eventually break.
This is not a theoretical concern. Security agencies already warn of “harvest now, decrypt later” attacks, where adversaries capture encrypted data today with the intention of decrypting it once quantum capability matures. That means sensitive information such as intellectual property, medical records, financial data, could be compromised retroactively, even if it seems safe now.
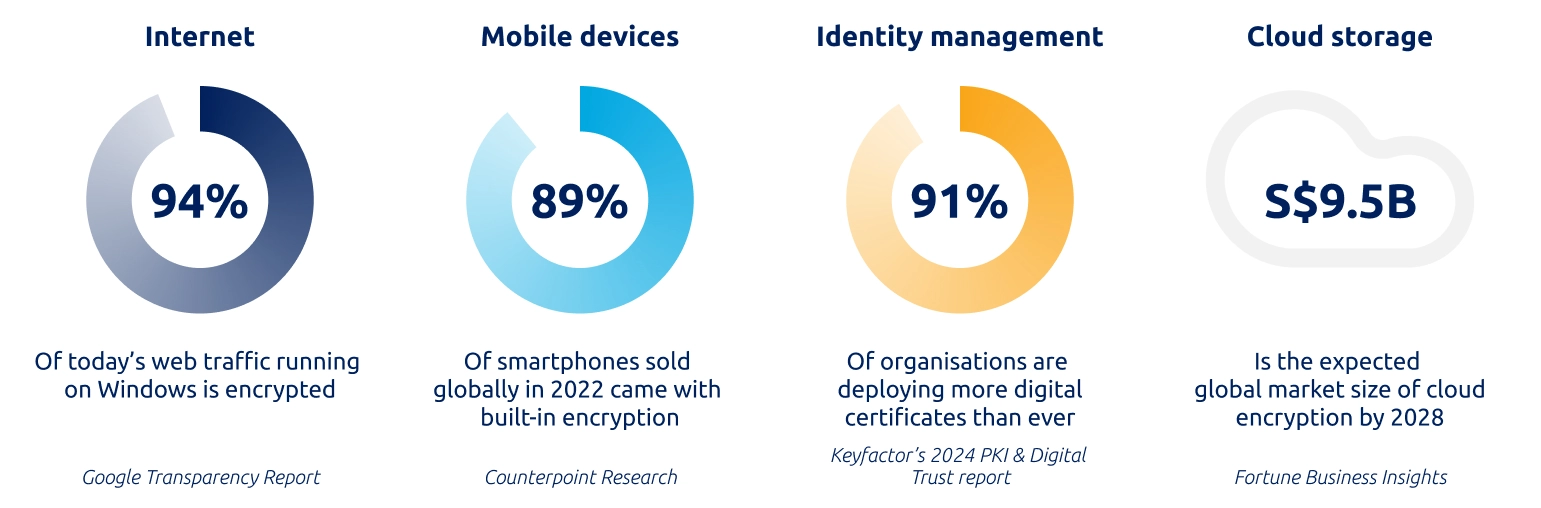
Figure 1: Statistics on the pervasiveness of cryptography.
A roadmap for readiness
Preparing for a quantum-safe future requires a structured approach. It is not about switching algorithms overnight, but about managing a staged migration that balances security, cost, and operational continuity.
Diagnosis
The journey begins with understanding where cryptography lives across your organisation. This means assessing which applications, systems, and business processes rely on encryption and discovering all certificates, keys, and algorithms that may be hidden deep within your infrastructure. Automated discovery tools are essential for achieving full visibility.
Planning
Once you know your cryptographic landscape, the next step is to design a quantum-safe strategy. This includes prioritising systems that protect long-lived or sensitive data and ensuring that new architectures are cryptographically agile and ready to adapt as standards and technologies evolve.
Execution
With priorities and architecture in place, organisations can begin deploying post-quantum cryptographic algorithms in a phased manner. Governance becomes a continuous loop: monitoring performance, updating standards, and ensuring compliance across hybrid environments that include both cloud and legacy systems.
The following figure illustrates this three-phase roadmap, from diagnosis and planning through to execution, providing a structured path for organisations to prepare for a quantum-safe future.
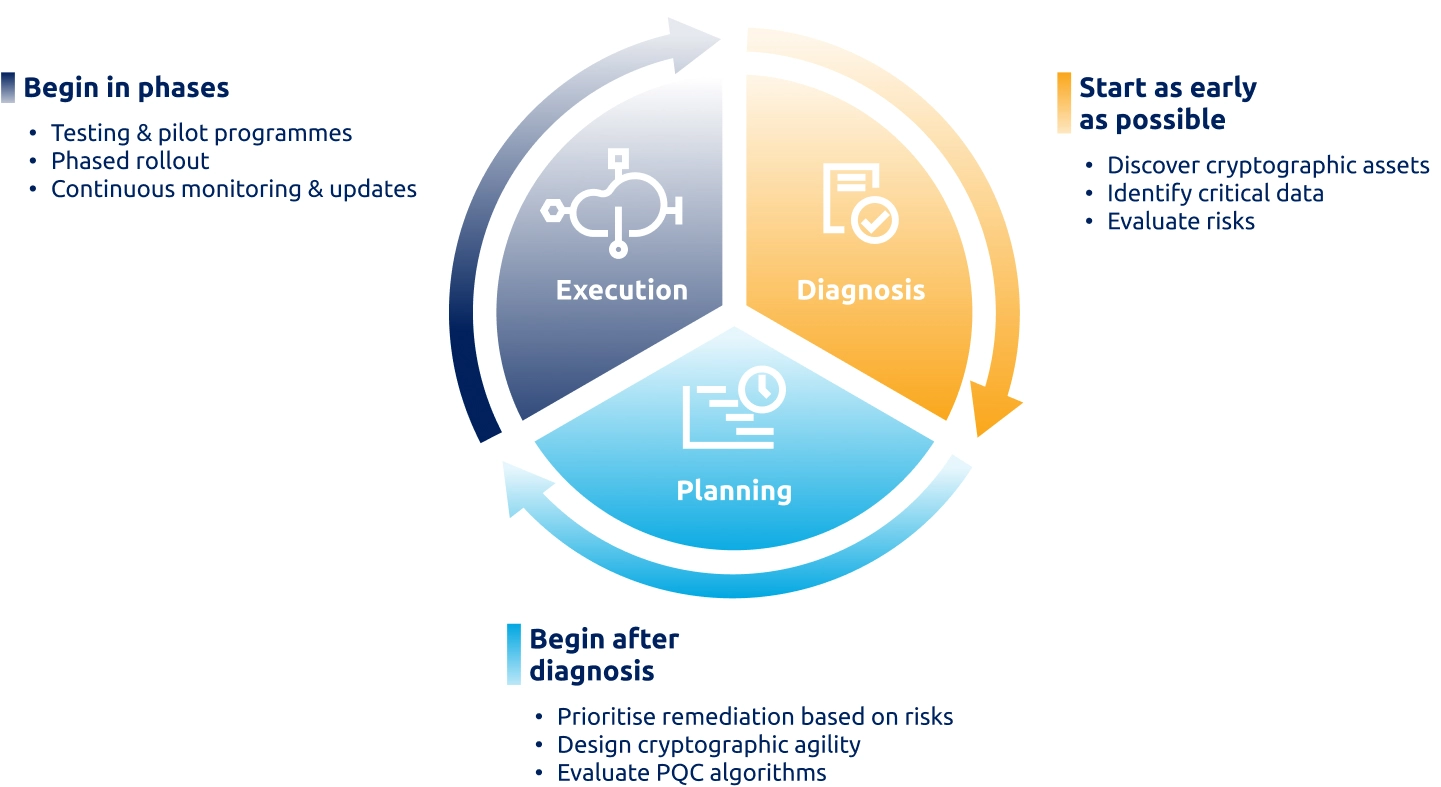
Figure 2: A proactive migration strategy.
This roadmap provides a proactive strategy that gives organisations the confidence to act today, even as PQC standards are finalised. It shifts the conversation from fear of disruption to readiness for opportunity.
The business case for acting early
For leadership teams, PQC migration is not only a technical exercise but also a strategic one. The risks of waiting too long include compliance failures, reputational damage, and the cost of rushed implementations. On the other hand, businesses that begin early can:
- Reduce migration costs. Industry data shows early movers can spend up to 40% less by spreading investment over time and avoiding emergency upgrades.
- Meet regulatory expectations. Governments and standards bodies are already signalling PQC adoption timelines. Preparing now avoids last-minute compliance pressures.
- Strengthen stakeholder trust. Customers, partners, and investors increasingly ask how organisations are preparing for future risks. Being able to show a quantum-safe plan builds confidence.
- Position for advantage. Quantum resilience can become a differentiator, especially in industries where data security is mission-critical, such as finance, healthcare, and public services.
Securing tomorrow starts today
Quantum disruption is inevitable, but it does not have to be destabilising. With a proactive strategy, organisations can take control of the migration journey rather than react under pressure when the threat becomes acute.
PQC is not simply a technical upgrade. It represents a shift in how businesses view resilience. Just as digital transformation redefined how organisations compete, quantum preparedness will define how they safeguard trust in the years ahead.
By starting today with assessment, discovery, and prioritisation, organisations can secure their future on their own terms, ensuring that when quantum technology arrives in full force, they are ready to meet it with confidence.
Take your next step toward a quantum-safe future
You’ve seen why PQC matters and what a proactive migration roadmap looks like. Now you can decide how deep you want to go.
Continue the journey
Learn how to uncover hidden cryptographic assets in Part 2: ‘Automating discovery of cryptographic assets’ — and see how NCS validates quantum-era security in Part 3: ‘Security validation of Quantum Key Distribution Networks’.
Go deeper
For a fuller picture, download our comprehensive guide 'Preparing for a quantum-safe future'.
References
[Cec24] L. Ceci. Number of unique WhatsApp mobile users worldwide from January 2020 to June 2024, Statista, 27 Aug 2024. https://www.statista.com/statistics/1306022/whatsapp-global-unique-users/
[Goo24] Google Transparency Report, HTTPS encryption on the web. https://transparencyreport.google.com/https/overview. Last accessed on 3 Oct 2024.
[Nes24] C. Neskey. Are your passwords in the green? Hive Systems. https://www.hivesystems.com/blog/are-your-passwords-in-the-green. Last accessed on 9 Oct 2024.
